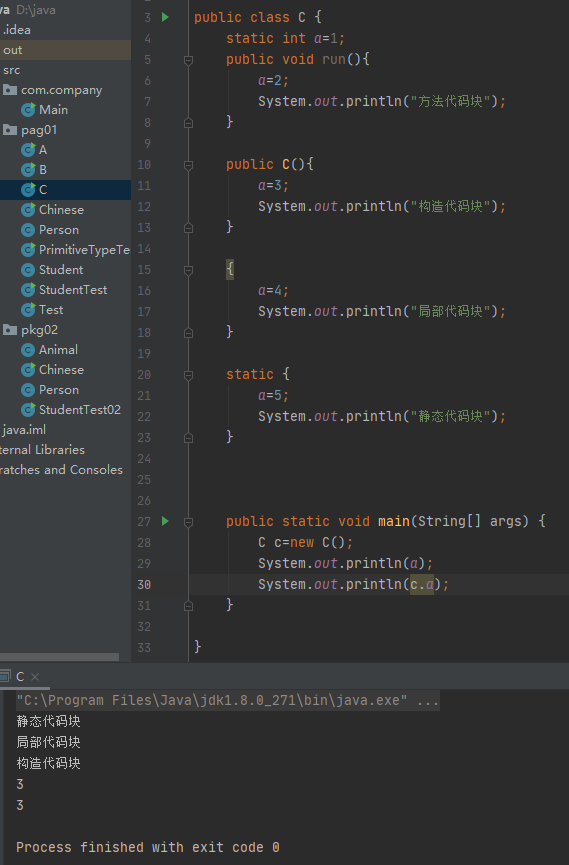
一,局部代码块
存在于方法里面(必须调用方法才可以)
public class Person{
public void run(){
System.out.println("局部代码块");
}
}
二,构造代码块
public class Person{
{
System.out.println("构造代码块");
}
}
三,静态代码块
public class Person{
static {
System.out.println("静态代码块");
}
}
四,同步代码块
synchronized(this) {
}
五,四种代码块执行顺序
静态代码块-->构造代码块-->构造函数-->局部代码块-->同步代码块
adb相关基础知识集锦
我所理解的OOP——UML六种关系
据说每个大牛、小牛都应该有自己的库——DOM处理续
据说每个大牛、小牛都应该有自己的库——DOM处理
JavaScript 继承
据说每个大牛、小牛都应该有自己的库——Event处理
据说每个大牛、小牛都应该有自己的库——框架篇
可拖动的DIV续
CSS hack前传——背景图片全屏
Copyright © 2011-2022 走看看