1.What is Delegation?
Just like the name. Delegation is that a server pretend to behalf of a user and to authenticate with kerberos protocol.There are three kinds of delegations.
| Kinds of Delegations | Limitions | Protocol | Note |
|---|---|---|---|
| Unconstrained Delegation | None | Just forward the TGT ticket which is able to be forwarded | None |
| Constrained Delegation | Front-End Server decide which Back-End service can receive delegation | 1.S4U2Proxy -> Forward the TGT ticket 2.S4U2Self -> Receive information of NTLM Authentication(Username&NTLM-Hash) And use that to get TGT and send TGT and receive TGS from KDC |
AD administrator account |
| Resource-Based Constrained Delegation | Back-End Services decide which Front-End service's delegation can be received | The same as Constrained Delegation | 1.S4U2Proxy -> Can Forward TGT ticket which is not to be able to forwarded. 2.You can use this cross the domain. 3.Service administrator account |
2.Unconstrained Delegation
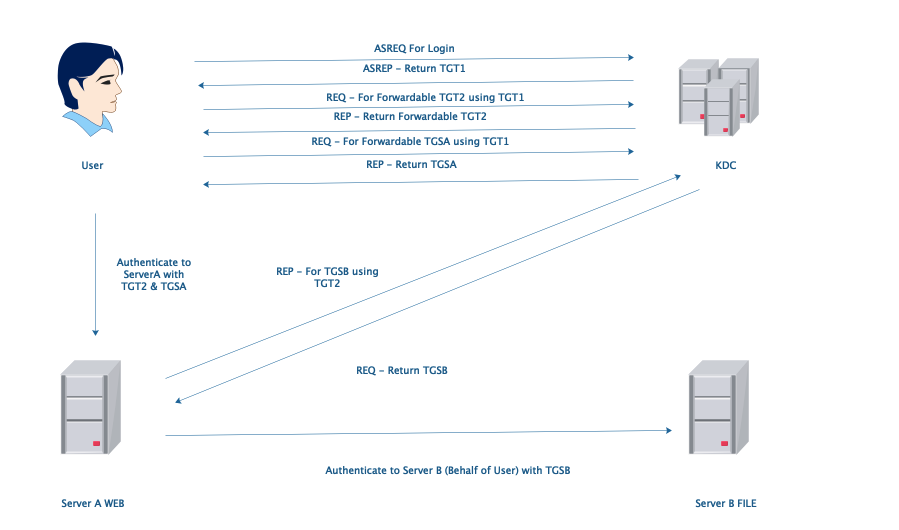
Unconstrained Delegation: ServerA can authenticate to any server in this domain behalf of user with TGT2. It is too dangerous.
3.Constrained Delegation
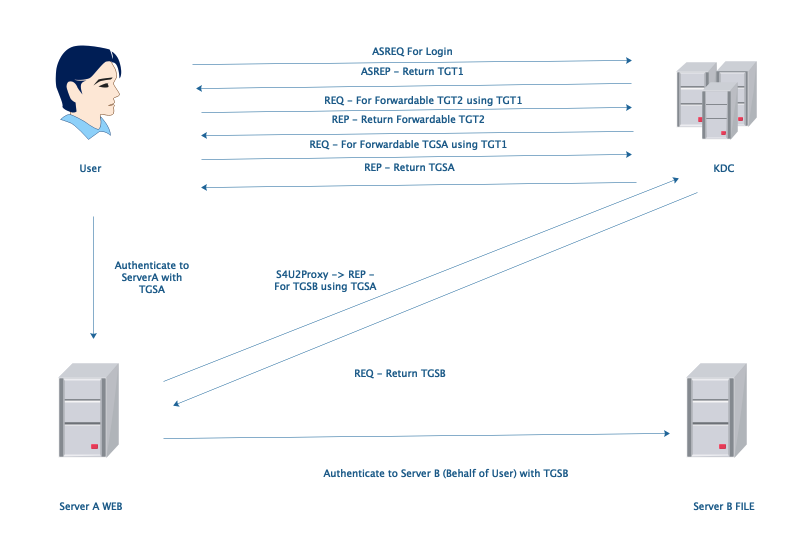
Only S4U2Proxy is what we need, if user use kerberos ticket to authenticate. Otherwise we need both S4U2Self and S4U2Proxy if user use NTLM hash to authenticate. In this condition, AD administrators can configure which service(SPNs) can receive ServerA’s delegation in ServerA's msDC-AllowedToDelegateTo property.
4.Resource-Based Constrained Delegation
There is one important difference between Constrained Delegation and Resource-Based Constrained Delegation. In Constrained Delegation, administrators of AD can configure which service can receive ServerA's delegation in their msDS-AllowedToActOnBehalfOfOtherIdentity properties. However, In Resource-Based Constrained Delegation, administrators of services can decide if those service will receive the ServerA's delegation or not. And it should be configured on the computers which is running those services. Do you think Resource-Based Constrained Delegation is much more safe than Constrained Delegation? No, Resource-Based Constrained Delegation has a big problem. In this condition, S4U2Proxy can forward unforwardable TGT and KDC will return TGS back. So if we could get the TGT which is not able to forward, We also could use it to do something bad.
5. What we can do to make it a little more safe?
** We can do a lot of things to make it more safe. Plus, the first one is to configure like this.**