CA与web在同一台虚拟机
HTTPD + Openssl = HTTPS
配置CA服务器
========================================================
1.配置CA 生成CA自己的公钥 私钥 CA对自己进行证书自签名 (用脚本生成)
[root@ws1 ~]# vim /etc/pki/tls/openssl.cnf
169 # This goes against PKIX guidelines but some CAs do it and some software 170 # requires this to avoid interpreting an end user certificate as a CA. 171 172 basicConstraints=CA:TURE
[root@ws1 ~]# /etc/pki/tls/misc/CA -newca CA certificate filename (or enter to create) Making CA certificate ... Generating a 2048 bit RSA private key .......................+++ .............+++ writing new private key to '/etc/pki/CA/private/./cakey.pem' Enter PEM pass phrase: Verifying - Enter PEM pass phrase: 设置私钥密码 ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:panda Organizational Unit Name (eg, section) []:it Common Name (eg, your name or your server's hostname) []:ca.panda.com Email Address []:ca@panda.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for /etc/pki/CA/private/./cakey.pem: Check that the request matches the signature Signature ok
Certificate Details: Serial Number: bd:c6:a3:34:68:2e:67:b9 Validity Not Before: Jul 29 12:10:07 2019 GMT Not After : Jul 28 12:10:07 2022 GMT Subject: countryName = cn stateOrProvinceName = beijing organizationName = panda organizationalUnitName = it commonName = ca.panda.com emailAddress = ca@panda.com X509v3 extensions: X509v3 Subject Key Identifier: 92:99:A7:72:67:24:08:6B:91:98:54:B1:A7:13:81:84:F6:89:D8:4C X509v3 Authority Key Identifier: keyid:92:99:A7:72:67:24:08:6B:91:98:54:B1:A7:13:81:84:F6:89:D8:4C X509v3 Basic Constraints: CA:TRUE Certificate is to be certified until Jul 28 12:10:07 2022 GMT (1095 days) Write out database with 1 new entries Data Base Updated
etc/pki/CA/private/cakey.pem CA私钥
/etc/pki/CA/cacert.pem CA证书
/etc/pki/CA/careq.pem CA证书请求
配置web服务器
===============================================================
web 生成自己的私钥
[root@ws1 ~]# openssl genrsa -des3 -out /etc/httpd/conf.d/server.key Generating RSA private key, 2048 bit long modulus ..........................+++ ......................................................................................... ...................................+++e is 65537 (0x10001) Enter pass phrase for /etc/httpd/conf.d/server.key: Verifying - Enter pass phrase for /etc/httpd/conf.d/server.key:
生成证书请求(使用身份标识+公钥)
[root@ws1 ~]# openssl req -new -key /etc/httpd/conf.d/server.key -out /etc/httpd/conf.d/s erver.csrEnter pass phrase for /etc/httpd/conf.d/server.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:panda Organizational Unit Name (eg, section) []:it 这几行必须与CA服务器的一致 Common Name (eg, your name or your server's hostname) []:www.wangs.com Email Address []:www@wangs.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
CA服务器对证书请求进行数字签名
=============================================================================
[root@ws1 ~]# openssl ca -keyfile /etc/pki/CA/private/cakey.pem -cert /etc/pki/CA/cacert .pem -in /etc/httpd/conf.d/server.csr -out /etc/httpd/conf.d/server.crtUsing configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for /etc/pki/CA/private/cakey.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: bd:c6:a3:34:68:2e:67:ba Validity Not Before: Jul 29 12:32:05 2019 GMT Not After : Jul 28 12:32:05 2020 GMT Subject: countryName = cn stateOrProvinceName = beijing organizationName = panda organizationalUnitName = it commonName = www.wangs.com emailAddress = www@wangs.com X509v3 extensions: X509v3 Basic Constraints: CA:TRUE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 63:7B:00:92:89:A6:3F:B5:B5:B7:57:6B:33:05:5A:51:83:0F:B7:31 X509v3 Authority Key Identifier: keyid:92:99:A7:72:67:24:08:6B:91:98:54:B1:A7:13:81:84:F6:89:D8:4C Certificate is to be certified until Jul 28 12:32:05 2020 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
如果失败:
方法一: [root@vlnx251106 ~]# rm /etc/pki/CA/index.txt [root@vlnx251106 ~]# touch /etc/pki/CA/index.txt 方法二: [root@vlnx251106 ~]# cat /etc/pki/CA/index.txt.attr unique_subject = yes --> no
配置web支持ssl实现https
==========================================================
[root@ws1 ~]# yum install mod_ssl -y
[root@ws1 ~]# vim /etc/httpd/conf.d/ssl.conf
95 # Server Certificate: 96 # Point SSLCertificateFile at a PEM encoded certificate. If 97 # the certificate is encrypted, then you will be prompted for a 98 # pass phrase. Note that a kill -HUP will prompt again. A new 99 # certificate can be generated using the genkey(1) command. 100 SSLCertificateFile /etc/httpd/conf.d/server.crt 101 102 # Server Private Key: 103 # If the key is not combined with the certificate, use this 104 # directive to point at the key file. Keep in mind that if 105 # you've both a RSA and a DSA private key you can configure 106 # both in parallel (to also allow the use of DSA ciphers, etc.) 107 SSLCertificateKeyFile /etc/httpd/conf.d/server.key
[root@ws1 ~]# systemctl restart httpd Enter SSL pass phrase for 192.168.88.101:443 (RSA) : ******
[root@ws1 ~]# netstat -tunpl | grep 443 tcp6 0 0 :::443 :::* LISTEN 5151/http d
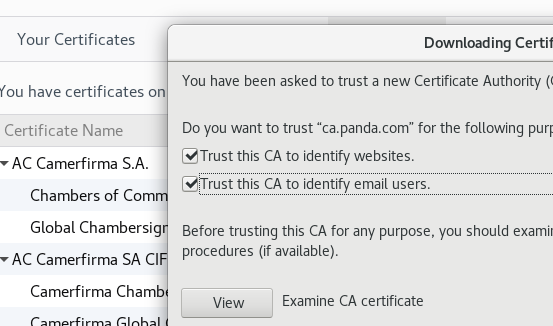
Client下载CA证书并导入到浏览器,然后访问www服务器
[root@ws1 ~]# scp /etc/pki/CA/cacert.pem 192.168.88.105:/tmp/ root@192.168.88.105's password: cacert.pem 100% 4438 91.6KB/s 00:00
打开一个图形化界面的虚拟机

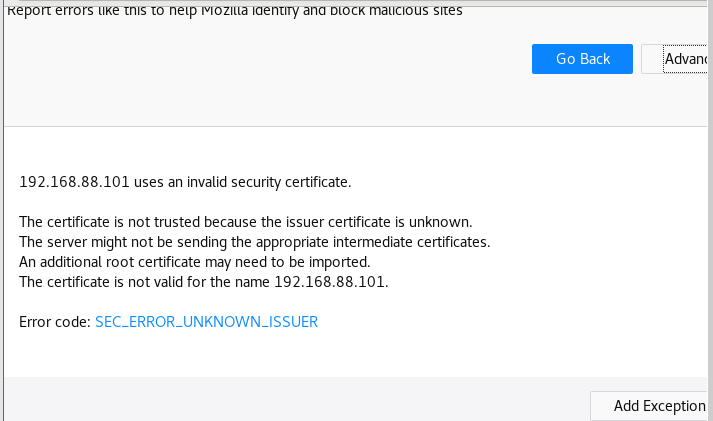
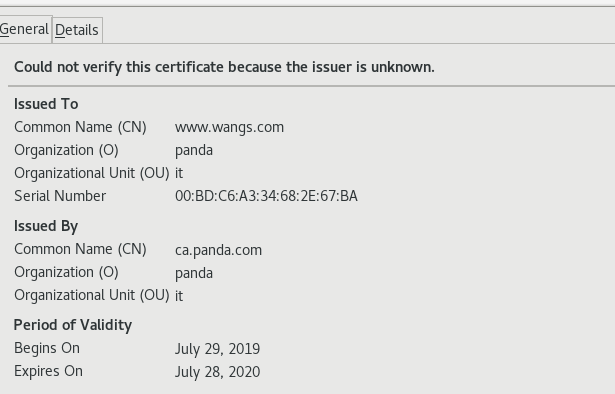
打开火狐浏览器的设置,然后点privacy & security