读计算机应该就同说过TCP/IP三次握手,但是都没有去验证过,今天心血来潮,去验证了一下,于是乎写下了这篇博客,可能写的可能有问题,还请多多指教
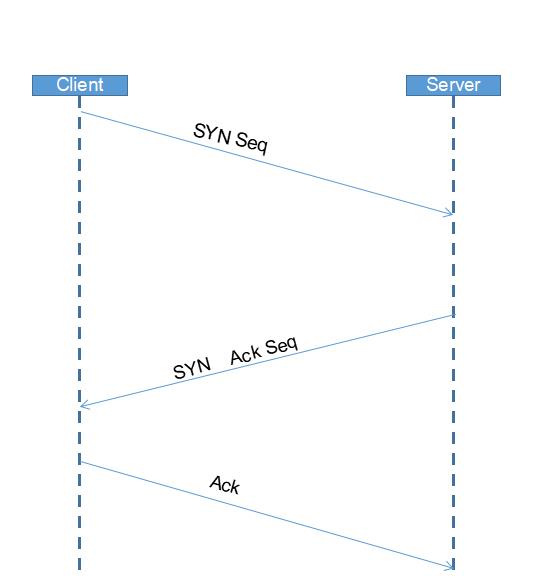
包括我学习,还有从很多资料来看资料,第三次握手,应该会返回ack(上一个seq+1),但是我从抓包,并没有发现,第三次只会返回一个ack,希望有人来解答一下这个问题
抓包如下(用黄色的勾画起来的):
09:52:52.462194 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [S], seq 3925850975, win 65535, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 E..4x.@.@.@z...n...m...P..._........r............... 09:52:52.462222 IP localhost.localdomain.http > 192.168.0.110.54420: Flags [S.], seq 2302688839, ack 3925850976, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 E..4..@.@......m...n.P...@>G...`..r..R.............. 09:52:52.462491 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [.], ack 1, win 1024, length 0 E..(x.@.@.@....n...m...P...`.@>HP............. 09:52:52.462628 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [P.], seq 1:223, ack 1, win 1024, length 222: HTTP: GET /favicon.ico HTTP/1.1 E...x @.@.?....n...m...P...`.@>HP.......GET /favicon.ico HTTP/1.1
这次我们就利用tcpdump来验证一下TCP/IP三次握手
要使用tcpdump抓包,首先要清楚工具输出的信息,默认tcpdump输出格式为
src > dst: Flags [tcpflags], seq data-seqno, ack ackno, win window, urg urgent, options [opts], length len
src > dst 目标源IP 端口 和 目标IP 端口
tcpflags
Tcpflags are some combination of S (SYN), F (FIN), P (PUSH), R (RST), U (URG), W (ECN CWR), E (ECN-Echo) or '.' (ACK), or 'none' if no flags are set.
S: SYN 同步 SYN = 1 表示这是一个连接请求或连接接受报文
F: FIN 用来释放一个连接.FIN=1 表明此报文段的发送端的数据已发送完毕,并要求释放运输连接
P: PUSH 接收 TCP 收到 PSH = 1 的报文段,就尽快地交付接收应用进程,而不再等到整个缓存都填满了后再向上交付
R: RST 当 RST=1 时,表明 TCP 连接中出现严重差错(如由于主机崩溃或其他原因),必须释放连接,然后再重新建立运输连接
.: 为ACK,表示响应
使用tcpdump抓取本机80端口的包
[root@localhost ~]# tcpdump -i enp0s8 port 80 -A
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on enp0s8, link-type EN10MB (Ethernet), capture size 262144 bytes
09:52:52.462194 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [S], seq 3925850975, win 65535, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
E..4x.@.@.@z...n...m...P..._........r...............
09:52:52.462222 IP localhost.localdomain.http > 192.168.0.110.54420: Flags [S.], seq 2302688839, ack 3925850976, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
E..4..@.@......m...n.P...@>G...`..r..R..............
09:52:52.462491 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [.], ack 1, win 1024, length 0
E..(x.@.@.@....n...m...P...`.@>HP.............
09:52:52.462628 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [P.], seq 1:223, ack 1, win 1024, length 222: HTTP: GET /favicon.ico HTTP/1.1
E...x @.@.?....n...m...P...`.@>HP.......GET /favicon.ico HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; Trident/7.0; rv:11.0) like Gecko
Host: 192.168.0.109
Connection: Keep-Alive
09:52:52.462638 IP localhost.localdomain.http > 192.168.0.110.54420: Flags [.], ack 223, win 237, length 0
E..(.&@.@..}...m...n.P...@>H...>P....F..
09:52:52.463084 IP localhost.localdomain.http > 192.168.0.110.54420: Flags [P.], seq 1:325, ack 223, win 237, length 324: HTTP: HTTP/1.1 404 Not Found
E..l.'@.@..8...m...n.P...@>H...>P.......HTTP/1.1 404 Not Found
Server: nginx/1.14.2
Date: Wed, 17 Apr 2019 13:52:52 GMT
Content-Type: text/html
Content-Length: 169
Connection: keep-alive
<html>
<head><title>404 Not Found</title></head>
<body bgcolor="white">
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.14.2</center>
</body>
</html>
09:52:52.463219 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [.], ack 325, win 1022, length 0
E..(x!@.@.@....n...m...P...>.@?.P.............
09:52:54.652738 IP 192.168.0.110.54420 > localhost.localdomain.http: Flags [R.], seq 223, ack 325, win 0, length 0
E..(x#@.@.@....n...m...P...>.@?.P.............
^C
8 packets captured
8 packets received by filter
0 packets dropped by kernel
[root@localhost ~]#
分析: 03:07:29.669315 IP 192.168.56.1.56572 > localhost.localdomain.http: Flags [S], seq 2538461989, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 客户端向发送SYN请求,seq为2538461989 03:07:29.669366 IP localhost.localdomain.http > 192.168.56.1.56572: Flags [S.], seq 643447264, ack 2538461990, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 服务器接受来自客户端的请求ack为2538461990(上次请求的seq + 1) , 并且发送 seq 为643447264 03:07:29.669632 IP 192.168.56.1.56572 > localhost.localdomain.http: Flags [.], ack 1, win 2053, length 0 客户端向服务器发送一个为ack
使用Wireshark分析
# tcpdump -i enp0s8 -w dump.pcap

可以清晰的看到TCP/IP的三次交互