姊妹篇:[https][tls] 如何使用wireshark查看tls/https加密消息
一,编译,启用strongswan的save-keys plugin
./configure --prefix=/root/OUTPUT --exec-prefix=/root/OUTPUT --enable-save-keys CFLAGS="-g -O0"
运行之前验证一下,是否加载了这个插件
[root@T9 OUTPUT]# ./sbin/swanctl --stat |grep save loaded plugins: charon aes save-keys des rc2 sha2 sha1 md5 mgf1 random nonce x509 revocation constraints pubkey
pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem fips-prf gmp curve25519 xcbc cmac hmac attr kernel-netlink
resolve socket-default stroke vici updown xauth-generic counters
二,增加如下配置
charon { load_modular = yes plugins { include strongswan.d/charon/*.conf save-keys { esp = yes ike = yes load = yes wireshark_keys = /root/OUTPUT/etc/keys } }
详细的解释,可以查man手册
charon.plugins.save-keys.esp [no] Whether to save ESP keys. charon.plugins.save-keys.ike [no] Whether to save IKE keys. charon.plugins.save-keys.load [no] Whether to load the plugin. charon.plugins.save-keys.wireshark_keys [] Directory where the keys are stored in the format supported by Wireshark. IKEv1 keys are stored in the ikev1_decryption_table file.
IKEv2 keys are stored in the ikev2_decryption_table file.
Keys for ESP CHILD_SAs are stored in the esp_sa file.
三,正常运行之后,这个目录下,就会存着key了,同时把包抓下来
./sbin/swanctl --load-all
./sbin/ipsec up net-net
查看保存的key
[root@T9 OUTPUT]# ll etc/keys/ total 8 -rw-r--r-- 1 root root 410 Dec 20 17:42 esp_sa -rw-r--r-- 1 root root 284 Dec 20 17:42 ikev2_decryption_table
四,配置wireshark
IKE:
edit->preferences->protocols->ISAKMP->IKEv2 Decryption Table->Edit
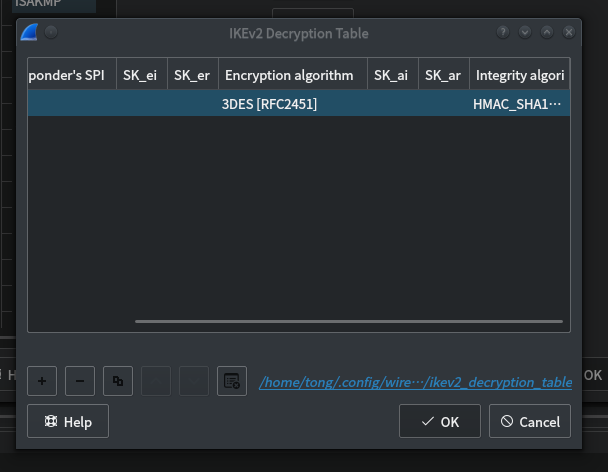
如图,看见这后边有个蓝色的文件名。
用前边获得的那个文件覆盖它。
cp ikev2_decryption_table /home/tong/.config/wireshark/ikev2_decryption_table
ESP:
edit->preferences->protocols->ESP->Edit
然后点加号,编辑
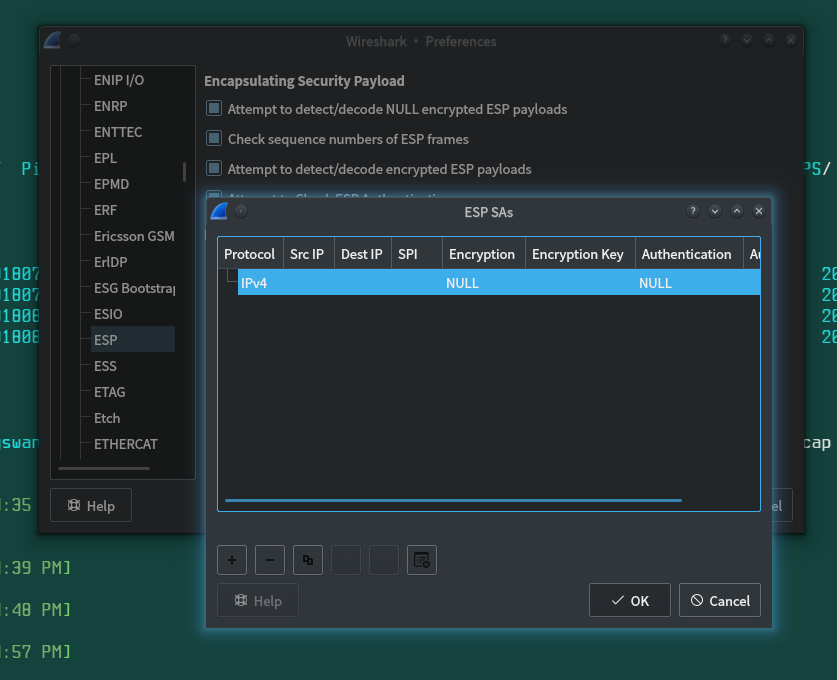
或者。直接cp进去到配置目录
cp esp_sa /home/tong/.config/wireshark/
五。用wirshark再次打开之前抓到的pcap包。
好了。现在的IKEV2和ESP都是解密过的了。
