API Server 内部通过用户认证后,然后进入授权流程。对合法用户进行授权并且随后在用户访问时进行鉴权,是权限管理的重要环节。
在 kubernetes 集群中,各种操作权限是赋予角色(Role 或者 ClusterRole)的。通过创建 RoleBinding 或者 ClusterBinding 把 用户(User),用户组(Group)或服务账号(Service Account)绑定在 Role 或 ClusterRole 上。这样用户,用户组或者服务账号就有了相对应的操作权限。
这里有个需要注意的地方
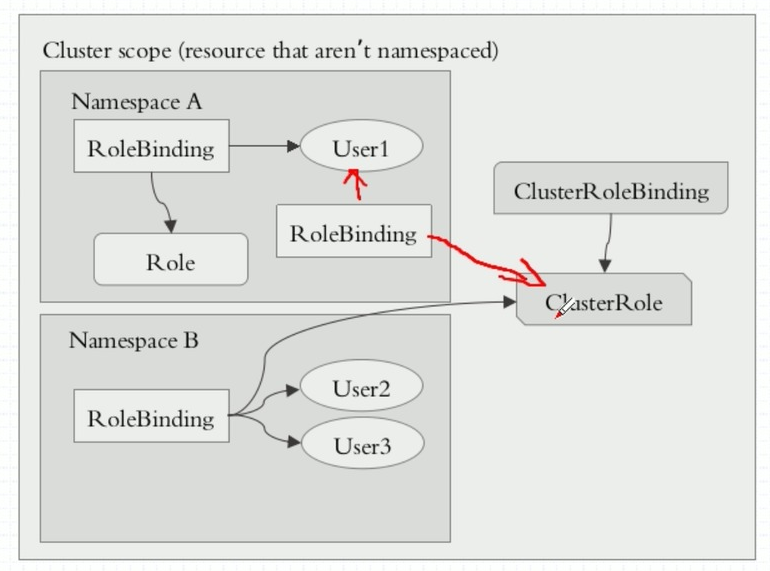
ClusterRoleBinding 只能绑定 ClusterRole,而 RoleBinding 可以绑定 Role 或者 ClusterRole。
根据上图:
1.User1 通过 RoleBinding 把 Role 绑定,可以在 Namespace A 获得 Role 中的权限;
2.User2 和 User3 通过 RoleBinding 把 ClusterRole 绑定,这两个用户即可以在 Namespace B 空间中获得 ClusterRole 权限;
3.如果 User1 通过 ClusterRoleBinding 把 ClusterRole 绑定,这个用户即可在所有的 Namespace 空间中获得 ClusterRole 权限;
创建 role
su - klvchen
cd sa/
kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml > role-demo.yaml
kubectl apply -f role-demo.yaml
kubectl get role
kubectl describe role pods-reader
创建 rolebinding
kubectl create rolebinding klvchen-read-pods --role=pods-reader --user=klvchen --dry-run -o yaml > rolebinding-demo.yaml
kubectl apply -f rolebinding-demo.yaml
kubectl describe rolebinding klvchen-read-pods
测试账号
kubectl config use-context klvchen@kubernetes
kubectl config view
kubectl get pods
为了方便测试,创建一个新的用户 ik8s
useradd ik8s
cp -rf .kube/ /home/ik8s/
chown -R ik8s. /home/ik8s/
su - ik8s
kubectl config use-context klvchen@kubernetes
kubectl config view
创建 clusterrole
kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run > clusterrole-demo.yaml
kubectl apply -f clusterrole-demo.yaml
kubectl get rolebinding
# 删除 klvchen-read-pods ,解除 role 角色 pods-reader 和 user 用户 klvchen 的绑定关系
kubectl delete rolebinding klvchen-read-pods
创建 clusterrolebinding
kubectl create clusterrolebinding klvchen-read-all-pods --clusterrole=cluster-reader --user=klvchen --dry-run -o yaml > clusterrolebinding-demo.yaml
kubectl apply -f clusterrolebinding-demo.yaml
kubectl describe clusterrolebinding klvchen-read-all-pods
测试
#切换到 ik8s 账户
kubectl get pods -n kube-system
# 所有命名空间都可以正常显示 pods
使用 rolebinding 关联 clusterrole
kubectl delete clusterrolebinding klvchen-read-all-pods
kubectl create rolebinding klvchen-read-pods --clusterrole=cluster-reader --user=klvchen --dry-run -o yaml > rolebinding-clusterrole-demo.yaml
kubectl apply -f rolebinding-clusterrole-demo.yaml
#测试
#切换到 ik8s 账户
kubectl get pods
# 只有默认的命名空间可以正常显示 pods
查看 k8s 集群中 admin 拥有的权限
kubectl get clusterrole admin -o yaml
kubectl get clusterrolebinding cluster-admin -o yaml
[root@master ~]# kubectl get clusterrolebinding cluster-admin -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
creationTimestamp: 2018-11-07T10:12:36Z
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: cluster-admin
resourceVersion: "107"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterrolebindings/cluster-admin
uid: a6252a77-e275-11e8-8c94-cad98100ca95
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: Group
name: system:masters # admin 所在的组是 system:masters
# kubernetes-admin 是属于 system:masters 组
[root@master ~]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.0.205:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: klvchen
name: klvchen@kubernetes
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: klvchen
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
查看对应的证书,这里注意了,证书的有效期为1年
[root@master ~]# cd /etc/kubernetes/pki/
[root@master pki]# openssl x509 -in ./apiserver-kubelet-client.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 3302614080992031284 (0x2dd53e0237bbb234)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=kubernetes
Validity
Not Before: Nov 7 10:11:55 2018 GMT
Not After : Nov 7 10:11:56 2019 GMT
Subject: O=system:masters, CN=kube-apiserver-kubelet-client
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
...后面信息忽略