接上一篇:i.mx6 Android5.1.1 初始化流程之init进程
参考资料:http://blog.csdn.net/mr_raptor/article/category/799879 这个博客里的Android系统移植与平台开发系列
Android init.rc文件简单介绍
init.rc脚本是由Android中linux的第一个用户级进程init进行解析的。
init.rc 文件并不是普通的配置文件,而是由一种被称为“Android初始化语言”(Android Init Language,这里简称为AIL)的脚本写成的文件。
该文件在ROM中是只读的,即使有了root权限,可以修改该文件也没有。因为我们在根目录看到的文件只是内存文件的镜像。也就是说,android启动后,会将init.rc文件装载到内存。而修改init.rc文件的内容实际上只是修改内存中的init.rc文件的内容。一旦重启android,init.rc文件的内容又会恢复到最初的装载。想彻底修改init.rc文件内容的唯一方式是修改Android的ROM中的内核镜像(boot.img)。
init.rc的使用方法,可以参考说明文件system/core/init/readme.txt
如果想要修改启动过程只能修改init.c(system/core/init)或者init.rc(system/core/rootdir)里的内容
首先简单的说一下语法:
init.rc文件基本组成单位是section, section分为三种类型,分别由三个关键字(所谓关键字即每一行的第一列)来区分,这三个关键字是 on、service、import。
1、on类型的section表示一系列命令的组合, 例如:
on init export PATH /sbin:/system/sbin:/system/bin export ANDROID_ROOT /system export ANDROID_DATA /data
这样一个section包含了三个export命令,命令的执行是以section为单位的,所以这三个命令是一起执行的,不会单独执行, 那什么时候执行呢? 这是由init.c的main()所决定的,main()里在某个时间会调用action_for_each_trigger("init", action_add_queue_tail);这就把 ” on init “开始的这样一个section里的所有命令加入到一个执行队列,在未来的某个时候会顺序执行队列里的命令,所以调用
action_for_each_trigger()
的先后决定了命令执行的先后。
2、service类型的section表示一个可执行程序,例如:
service surfaceflinger /system/bin/surfaceflinger
class main
user system
group graphics drmrpc
onrestart restart zygote
surfaceflinger作为一个名字标识了这个service,/system/bin/surfaceflinger表示可执行文件的位置, class、user、group、onrestart这些关键字所对应的行都被称为options, options是用来描述的service一些特点,不同的service有着不同的options。service类型的section标识了一个service(或者说可执行程序), 那这个service什么时候被执行呢?是在class_start这个命令被执行的时候,这个命令行总是存在于某个on类型的section中,“class_start core”这样一条命令被执行,就会启动类型为core的所有service。如:
1 on boot 、、、、、、 class_start core class_start main
所以可以看出android的启动过程主要就是on类型的section被执行的过程。
3、import类型的section表示引入另外一个.rc文件,例如:
import init.test.rc
i.mx6 Android5.1.1 init.rc分析
#包含以下几个rc,然后全部打开,查找early-init import /init.environ.rc import /init.usb.rc #这里的ro.hardware是系统属性,可以通过greprop ro.hardware查看其值为:init.freescale.rc import /init.${ro.hardware}.rc import /init.zygote32.rc import /init.trace.rc
没找到,接着找
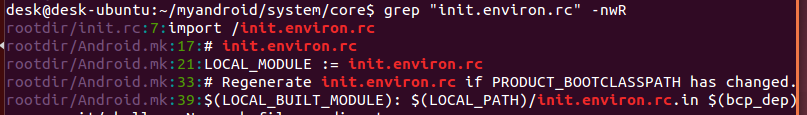
这里可以发现init.environ.rc为编译时候生成的,打开Android.mk,发现其生成后放入TARGET_ROOT_OUT中,打开查看
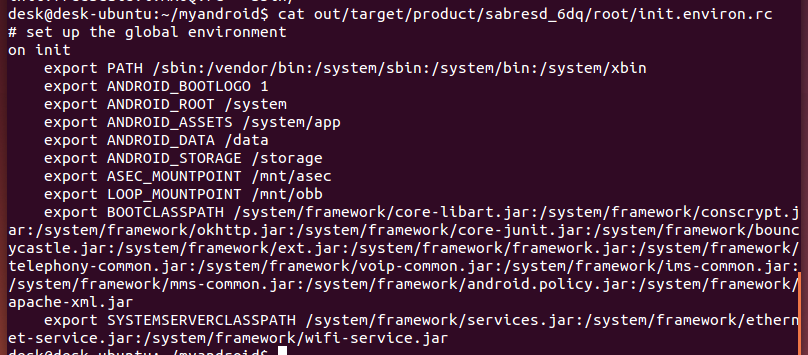
这里其实就是导出了几个环境变量
接着查看init.usb.rc目录,发现里面全部都是跟USB相关的配置
接着查看init.${ro.hardware}.rc

得知init.${ro.hardware}.rc=init.freescale.rc,这个也搜索不到,也是编译时候生成的。
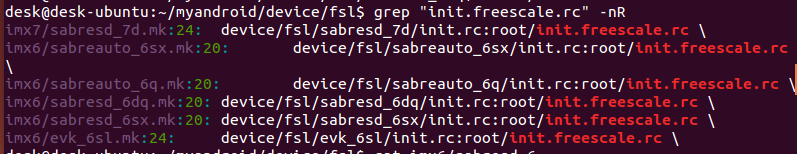
其编译在im6/sabresd_6dq.mk中,
on early-init # Set init and its forked children's oom_adj. write /proc/1/oom_score_adj -1000 # Apply strict SELinux checking of PROT_EXEC on mmap/mprotect calls. write /sys/fs/selinux/checkreqprot 0 # Set the security context for the init process. # This should occur before anything else (e.g. ueventd) is started. setcon u:r:init:s0 # Set the security context of /adb_keys if present. restorecon /adb_keys #启动ueventd进程 start ueventd # create mountpoints mkdir /mnt 0775 root system
2.查看init
on init sysclktz 0 loglevel 3 # Backward compatibility symlink /system/etc /etc symlink /sys/kernel/debug /d # Right now vendor lives on the same filesystem as system, # but someday that may change. symlink /system/vendor /vendor # Create cgroup mount point for cpu accounting mkdir /acct mount cgroup none /acct cpuacct mkdir /acct/uid # Create cgroup mount point for memory mount tmpfs none /sys/fs/cgroup mode=0750,uid=0,gid=1000 mkdir /sys/fs/cgroup/memory 0750 root system mount cgroup none /sys/fs/cgroup/memory memory write /sys/fs/cgroup/memory/memory.move_charge_at_immigrate 1 chown root system /sys/fs/cgroup/memory/tasks chmod 0660 /sys/fs/cgroup/memory/tasks mkdir /sys/fs/cgroup/memory/sw 0750 root system write /sys/fs/cgroup/memory/sw/memory.swappiness 100 write /sys/fs/cgroup/memory/sw/memory.move_charge_at_immigrate 1 chown root system /sys/fs/cgroup/memory/sw/tasks chmod 0660 /sys/fs/cgroup/memory/sw/tasks mkdir /system mkdir /data 0771 system system mkdir /cache 0770 system cache mkdir /config 0500 root root mkdir /device 0771 system system # See storage config details at http://source.android.com/tech/storage/ mkdir /mnt/shell 0700 shell shell mkdir /mnt/media_rw 0751 media_rw media_rw mkdir /storage 0751 root sdcard_r mkdir /mnt/media_rw/extsd 0755 system system symlink /mnt/media_rw/extsd /storage/extsd mkdir /mnt/media_rw/udisk 0755 system system symlink /mnt/media_rw/udisk /storage/udisk # Directory for putting things only root should see. mkdir /mnt/secure 0700 root root # Directory for staging bindmounts mkdir /mnt/secure/staging 0700 root root # Directory-target for where the secure container # imagefile directory will be bind-mounted mkdir /mnt/secure/asec 0700 root root # Secure container public mount points. mkdir /mnt/asec 0700 root system mount tmpfs tmpfs /mnt/asec mode=0755,gid=1000 # Filesystem image public mount points. mkdir /mnt/obb 0700 root system mount tmpfs tmpfs /mnt/obb mode=0755,gid=1000 # shared memory used by middleware mkdir /mnt/shm 0775 media syste mount tmpfs tmpfs /mnt/shm mode=0775,uid=1013,gid=1000,size=1m # memory control cgroup mkdir /dev/memcg 0700 root system mount cgroup none /dev/memcg memory write /proc/sys/kernel/panic_on_oops 1 write /proc/sys/kernel/hung_task_timeout_secs 0 write /proc/cpu/alignment 4 write /proc/sys/kernel/sched_latency_ns 10000000 write /proc/sys/kernel/sched_wakeup_granularity_ns 2000000 write /proc/sys/kernel/sched_compat_yield 1 write /proc/sys/kernel/sched_child_runs_first 0 write /proc/sys/kernel/randomize_va_space 2 write /proc/sys/kernel/kptr_restrict 2 write /proc/sys/vm/mmap_min_addr 32768 write /proc/sys/net/ipv4/ping_group_range "0 2147483647" write /proc/sys/net/unix/max_dgram_qlen 300 write /proc/sys/kernel/sched_rt_runtime_us 950000 write /proc/sys/kernel/sched_rt_period_us 1000000 # reflect fwmark from incoming packets onto generated replies write /proc/sys/net/ipv4/fwmark_reflect 1 write /proc/sys/net/ipv6/fwmark_reflect 1 # set fwmark on accepted sockets write /proc/sys/net/ipv4/tcp_fwmark_accept 1 # Create cgroup mount points for process groups mkdir /dev/cpuctl mount cgroup none /dev/cpuctl cpu chown system system /dev/cpuctl chown system system /dev/cpuctl/tasks chmod 0666 /dev/cpuctl/tasks write /dev/cpuctl/cpu.shares 1024 write /dev/cpuctl/cpu.rt_runtime_us 800000 write /dev/cpuctl/cpu.rt_period_us 1000000 mkdir /dev/cpuctl/bg_non_interactive chown system system /dev/cpuctl/bg_non_interactive/tasks chmod 0666 /dev/cpuctl/bg_non_interactive/tasks # 5.0 % write /dev/cpuctl/bg_non_interactive/cpu.shares 52 write /dev/cpuctl/bg_non_interactive/cpu.rt_runtime_us 700000 write /dev/cpuctl/bg_non_interactive/cpu.rt_period_us 1000000 # qtaguid will limit access to specific data based on group memberships. # net_bw_acct grants impersonation of socket owners. # net_bw_stats grants access to other apps' detailed tagged-socket stats. chown root net_bw_acct /proc/net/xt_qtaguid/ctrl chown root net_bw_stats /proc/net/xt_qtaguid/stats # Allow everybody to read the xt_qtaguid resource tracking misc dev. # This is needed by any process that uses socket tagging. chmod 0644 /dev/xt_qtaguid # Create location for fs_mgr to store abbreviated output from filesystem # checker programs. mkdir /dev/fscklogs 0770 root system # pstore/ramoops previous console log mount pstore pstore /sys/fs/pstore chown system log /sys/fs/pstore/console-ramoops chmod 0440 /sys/fs/pstore/console-ramoops
device/fsl/sabresd_6dq/init.freescale.rc
on init start watchdogd # See storage config details at http://source.android.com/tech/storage/ mkdir /mnt/shell/emulated 0700 shell shell mkdir /storage/emulated 0555 root root export EXTERNAL_STORAGE /storage/emulated/legacy export EMULATED_STORAGE_SOURCE /mnt/shell/emulated export EMULATED_STORAGE_TARGET /storage/emulated # Support legacy paths symlink /storage/emulated/legacy /sdcard symlink /storage/emulated/legacy /mnt/sdcard symlink /storage/emulated/legacy /storage/sdcard0 symlink /mnt/shell/emulated/0 /storage/emulated/legacy # setup the global environment export SHM_MOUNTPOINT /mnt/shm export LIGHTSENSOR_PATH /sys/class/i2c-adapter/i2c-1/1-0044 export VPU_FW_PATH /system/lib/firmware/vpu export CODEC_SHM_PATH /mnt/shm export CORE_REGISTER_FILE /system/etc/core_register export COMPONENT_REGISTER_FILE /system/etc/component_register export CONTENTPIPE_REGISTER_FILE /system/etc/contentpipe_register # disable cursor blink for fbcon, if no splash screen support write /sys/class/graphics/fbcon/cursor_blink 0 # deattch the fbcon as hdmi hotplug conflict with fbcon write /sys/class/vtconsole/vtcon1/bind 0
3.查看late-init
on late-init trigger early-fs trigger fs trigger post-fs trigger post-fs-data # Load properties from /system/ + /factory after fs mount. Place # this in another action so that the load will be scheduled after the prior # issued fs triggers have completed. trigger load_all_props_action # Remove a file to wake up anything waiting for firmware. trigger firmware_mounts_complete trigger early-boot trigger boot
具体还没有完全分析清楚,太多了,其实.rc都会在out/target/product/sabresdq/里面生成,只是我都清除了,看不到了,稍后接着分析,但是还有两个比较重要的
1.在init.rc当中: i.mx6 Android5.1.1 servicemanager
#名字为servicemanager的服务,可执行文件的路径在/system/bin/servicemanager
#属于core类,用户为:system,用户组为:system
#critical:如果在几分钟内一直没响应则重启服务
#重启servicemanager需要冲入如下的服务healthd,zygote,media,surfaceflinger,drm
service servicemanager /system/bin/servicemanager class core user system group system critical onrestart restart healthd onrestart restart zygote onrestart restart media onrestart restart surfaceflinger onrestart restart drm
2.在init.rc中导入的init.zygote32.rc:i.mx6 Android5.1.1 zygote
#名字为zygote的服务,可执行文件路径为/system/bin/app_process,后面几个为带的参数
#建立socket通讯
#运行后,只执行一次的几个服务
service zygote /system/bin/app_process -Xzygote /system/bin --zygote --start-system-server class main socket zygote stream 660 root system onrestart write /sys/android_power/request_state wake onrestart write /sys/power/state on onrestart restart media onrestart restart netd
i.mx6 Android5.1.1 init.rc启动流程
其余的就不看了,直接看流程,在init.rc中有这么几个触发点:
on boot
。。。
class_start core
on nonencrypted
class_start main
class_start late_start
on property:vold.decrypt=trigger_encryption
start surfaceflinger
start encrypt
on charger
class_start charger
on property:vold.decrypt=trigger_restart_min_framework
class_start main
on property:vold.decrypt=trigger_restart_framework
class_start main
class_start late_start
根据之前分析出来的流程:early-init -->> init --> late-init
接着细分为:
early-init(启动ueventd)
init(创建一堆的文件,写文件,挂文件系统)
late-init
trigger early-fs
trigger fs //挂fstab.freescale里面的
trigger post-fs //挂fstab.freescale里面的
trigger post-fs-data //创建一堆的目录和数据
trigger load_all_props_action //加载所有属性??
trigger early-boot
trigger boot //这里跳到boot
boot(修改各种文件和目录的权限以及用户用户组,还有/device目录下的init.rc也差不多,启动看门狗,跳转至class core)
class core: 开始启动一堆的服务:
service ueventd /sbin/ueventd
logd /system/bin/logd
healthd /sbin/healthd
console /system/bin/sh
lmkd /system/bin/lmkd
servicemanager /system/bin/servicemanager //重点的native服务:这个服务通过binder机制来管理所有服务的添加和查询
vold /system/bin/vold
surfaceflinger /system/bin/surfaceflinger
bootanim /system/bin/bootanimation //开机动画
中间省略。。。
class main: 也是启动服务:
service media /system/bin/mediaserver //framework层C++服务:会启动所有的framework层的C++服务,并管理
service zygote /system/bin/app_process64 -Xzygote /system/bin --zygote --start-system-server //zygote服务:这个会启动所有JAVA服务,启动应用程序,还有一个重要的服务SystemServer