dashboard安装部署
由于会被墙, 所以要加一步拉取镜像
docker pull registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
docker tag registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
#把镜像copy到其他节点
docker save k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1 -o dashboard.tar
scp dashboard.tar 10.0.0.51:/root/
#在其他node节点导入镜像
docker load -i dashboard.tar
docker image ls|grep k8s.gcr.io/kubernetes-dashboard-amd64
正式部署, 一条命令
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
[root@master ~]# kubectl get svc -n kube-system #可以看到svc类型为ClusterIP
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 15d
kubernetes-dashboard ClusterIP 10.111.228.197 <none> 443/TCP 20m
dashboard默认采用的是ClusterIP, patch修改为NodePort, 以便可以直接访问(也可以采用ingress)
kubectl patch svc -n kube-system kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}'
[root@master ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 15d
kubernetes-dashboard NodePort 10.111.228.197 <none> 443:32094/TCP 23m
遇到的坑, 不能正常访问, 提示NET::ERR_CERT_INVALID
解决方式, 我们采取手动生成证书
| 可以看到这个Secret为空, Data处没有证书 |
kubectl describe secret kubernetes-dashboard-certs -n kube-system
Name: kubernetes-dashboard-certs
Namespace: kube-system
Labels: k8s-app=kubernetes-dashboard
Annotations:
Type: Opaque
Data
====
创建dashboard证书
mkdir -pv /etc/kubernetes/pki/dashboard && cd /etc/kubernetes/pki/
cp ca.crt ca.key dashboard/ && cd dashboard/
(umask 077;openssl genrsa -out dashboard.key 2048)
openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=wangtianpei/CN=dashboard" #如果要用域名访问, CN一定要和域名保持一致
openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 3650
#拷贝到各个节点
scp -r /etc/kubernetes/pki/dashboard/ node01:/etc/kubernetes/pki/
这里以hostpath的形式挂载到pod中
# 下载dashboard的yaml文件
wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
将文件中所有和secret相关的都注释掉
| 以下两段代码为注释掉的行 |
17 #apiVersion: v1
18 #kind: Secret
19 #metadata:
20 # labels:
21 # k8s-app: kubernetes-dashboard
22 # name: kubernetes-dashboard-certs
23 # namespace: kube-system
24 #type: Opaque
25 #
26 #---
136 # - name: kubernetes-dashboard-certs
137 # secret:
138 # secretName: kubernetes-dashboard-certs
| 以下两段代码为添加的行 |
139 - name: kubernetes-dashboard-certs
140 hostPath:
141 path: /etc/kubernetes/pki/dashboard
142 type: Directory
165 type: NodePort
创建dashboard
[root@master ~]# kubectl apply -f kubernetes-dashboard.yaml
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
[root@master ~]# kubectl get pod kubernetes-dashboard-64fc96f8b4-bm999 -n kube-system
NAME READY STATUS RESTARTS AGE
kubernetes-dashboard-64fc96f8b4-bm999 1/1 Running 0 28s
[root@master ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 26d
kubernetes-dashboard NodePort 10.101.252.179 <none> 443:31515/TCP 77s
访问https://10.0.0.50:31515
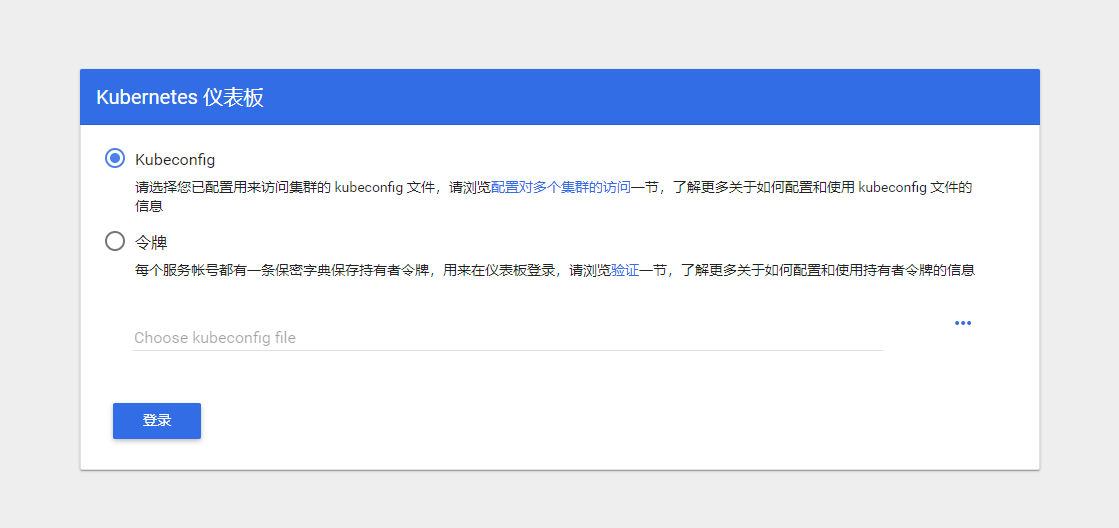
dashboard的两种认证方式
- kubeconfig
- token
token令牌认证
| 在kube-system名称空间创建一个名为dashboard-admin的ServiceAccount 将dashboard-admin这个ServiceAccount和cluster-admin绑定 |
cat > dashboard-admin.yaml << EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: dashboard-admin
namespace: kube-system
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: dashboard-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kube-system
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
EOF
[root@master ~]# kubectl apply -f dashboard-admin.yaml
serviceaccount/dashboard-admin created
clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created
查看serviceaccount生成的secret文件
[root@master ~]# kubectl get secret -n kube-system |grep dashboard-admin
dashboard-admin-token-twrjp kubernetes.io/service-account-token 3 80s
[root@master ~]# kubectl describe secret dashboard-admin-token-twrjp -n kube-system
Name: dashboard-admin-token-twrjp
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 4c2caffd-37fe-49ae-a443-d0b3e345da07
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdHdyanAiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNGMyY2FmZmQtMzdmZS00OWFlLWE0NDMtZDBiM2UzNDVkYTA3Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.OEaz9gm3ZB3jVxc4sp4peD4XwO-zPg5on4yV0u4UKpKa6mQcNF0qJ5f1mMO6AztZUPLSgsd46tu1p1ZOEh3FFCdlw7fRT2DSZsPFHP-4ahlJcEVD1egBHnQlvdoEo1Rhxkji157QjegCIu09TPe8m-2cd5Mlw_5rlOnMcJyJuGvyUIIqUi00AHXilEZ1kiI939HhKfqzJtnXwgNUEhmKcNHboGPt7yoKEaMHio-uHQoyQVUXSPXUWhvFtCq1La25oDJBV5SMO5cq3PqqDnCaPMNDLslMh8lv5mYzMvdrz-47hdhuMvc1-pR7LbD2J8hI0XxeAVWt9c4oATaQtj8vLA
ca.crt: 1025 bytes
namespace: 11 bytes
| 上面查看到的token就是用来登录dashboard的令牌 |
Kubeconfig文件认证
获取token, 注意token是base64加密的
[root@master ~]# kubectl get secret dashboard-admin-token-twrjp -n kube-system -o jsonpath={.data.token}
解密token
[root@master ~]# echo "上述命令获取到的token" | base64 -d
配置dashboard-admin的集群信息, 并将配置信息保存到/root/dashboard-admin.conf
kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server="https://10.0.0.50:6443" --embed-certs=true --kubeconfig=/root/dashboard-admin.conf
配置用户token信息, 并将配置信息保存到`/root/dashboard-admin.conf
kubectl config set-credentials dashboard-admin --token="上述命令获取到的token" --kubeconfig=/root/dashboard-admin.conf
配置上下文和当前上下文
kubectl config set-context dashboard-admin@kubernetes --cluster=kubernetes --user=dashboard-admin --kubeconfig=/root/dashboard-admin.conf
配置当前使用的上下文
kubectl config use-context dashboard-admin@kubernetes --kubeconfig=/root/dashboard-admin.conf
查看配置文件信息
kubectl config view --kubeconfig=/root/dashboard-admin.conf
| 可以通过dashboard-admin.conf 这个文件来登录dashboard |
创建只对default namespache有权限的token
和前边区别很小, 不做过多赘述
创建在指定namespace创建ServiceAccount, 然后通过rolebinding和clusterrole的admin进行绑定
kubectl create serviceaccount def-ns-admin -n default
kubectl create rolebinding df-ns-amdin --clusterrole=admin --serviceaccount=default:def-ns-admin #注意这里用的是rolebinding
[root@master ~]# kubectl get secrets -n default
NAME TYPE DATA AGE
admin-token-zwzps kubernetes.io/service-account-token 3 47h
def-ns-admin-token-ftl5t kubernetes.io/service-account-token 3 100s
[root@master ~]# kubectl describe secrets def-ns-admin-token-ftl5t
Name: def-ns-admin-token-ftl5t
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: def-ns-admin
kubernetes.io/service-account.uid: 7da89bde-2c1f-4dd0-87a5-79ca9b9e5454
Type: kubernetes.io/service-account-token
Data
====
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1mdGw1dCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI3ZGE4OWJkZS0yYzFmLTRkZDAtODdhNS03OWNhOWI5ZTU0NTQiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.utBN-Pc9ggRZAcfmQEW6sgHIxIGL8-m4xRy_YKw9LpGmfYMU9aGJcNh02fI4cPsoQhImisK36s3KqHudhD-Hdt9IsV0BnAMZsGYyjtdz_B8Z63MfobJO1EdpXQhXowtFDisVNdwJoyqgn9u8292gF2xOcUM6wG5MJMqvfzGoKVjlb-e4NUMrIj7GBN9rhiEj27dzh3jtjXlYB3hAOZh_sakh1Teuw1RQuiAlkQYNf6ixliYkT6Pz9_XRrpluLUVtVIC6Su7hTzvUn9MX6EzPs3ik8GqGw1O3AyEfxCb5390V6qsEd9iWLYoSZ-Ixl73QfGqls-cF3BBI9dSalYNbpQ
ca.crt: 1025 bytes
| 上面查看到的token就是用来登录dashboard的令牌, 并且只能看到default的资源 |