部署dashboard
$ wget https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml #修改文件内容 默认kubernetes-dashboard是官网默认镜像地址,需要翻墙,咱们这里用阿里云的镜像就可以。 ..... spec: containers: - name: kubernetes-dashboard image: registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.0 imagePullPolicy: IfNotPresent .... 修改svc的类型 ..... spec: type: NodePort ports: ..... 启动dashboard $ kubectl apply -f kubernetes-dashboard.yaml 查看是否启动成功 $ kubectl get pod -n kube-system .... NAME READY STATUS RESTARTS AGE kubernetes-dashboard-64767d465c-xgxhr 1/1 Running 0 17h 查看访问地址 $ kubectl get svc -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kubernetes-dashboard NodePort 10.103.15.27 <none> 443:30589/TCP 17h 随意一个node节点加暴露端口通过https访问访问。
如何生成一个dashboard专用证书
创建一个dashboard的私钥
(umask 077; openssl genrsa -out dashboard.key 2048)
生成一个证书签署请求
openssl req -new -key dashboard.key -out dashboard.crs -subj "/O=jaxzhai/CN=dashboard"
通过ca.key和ca.crt签署证书
openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 2048
通过签署证书创建一个sercert
kubectl create secret generic dashboard-cert -n kube-system --from-file=dashboard.crt=./dashboard.crt --from-file=dashboard.key=./dashboard.key
kubernetes-dashboard有两种认证方式,一个token认证,另一个是Kubeconfig文件的认证。这个时候的认证不是UserAccount而是获取kubernetes集群资源信息的serviceAccount,下面演示两种认证
token认证
创建一个serviceaccount并绑定集群管理员角色
$ vim serviceaccount-rbac.yaml
# ------------------- Dashboard Service Account ------------------- # apiVersion: v1 kind: ServiceAccount metadata: name: dashboard-admin namespace: kube-system --- # -------------------Dashboard Service Account rbac ------------------- # apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: dashboard-cluster-admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kube-system $ kubectl apply -f serviceaccount-rbac.yaml serviceaccount/dashboard-admin created clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
查看serviceaccount 的token
$ kubectl describe secret dashboard-admin-token-n7z7p -n kube-system Name: dashboard-admin-token-n7z7p Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name=dashboard-admin kubernetes.io/service-account.uid=3b1aa9ff-e25c-11e8-b8c9-005056930126 Type: kubernetes.io/service-account-token Data ==== token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbjd6N3AiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiM2IxYWE5ZmYtZTI1Yy0xMWU4LWI4YzktMDA1MDU2OTMwMTI2Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.V3hE7CTjopp8QpoPsArLH5jhLiiQChbrDT88ksb8lpAKfQMKeTjqmsVKYo6Li1HxOYH85m6n6E2f6q25PDsU0hfWEWSXvVYB5vRF-wC1ty5VqcpVIBqbEZAa9kbwaEyI8PeFgDiP1v_eHXgbBRvXoEWCl1Rg5x5Tqy0ov5ezFov-ohMAiibl0q_97eKXHQKTptdzqrSak_TeB2IDywpeKJOi4jaadVA8SZDRMf7wy7NPF5gNUK39M9XmFyNk6V07sDWY8t3wRTrxZFSAY7xTJTZFy3-D49WJ9QKYRSZlAHn7UD7TJ35HnH1XbApAiR4j0yZo9mTH2aSWIkABZ3N86w ca.crt: 1025 bytes namespace: 11 bytes
登录一下
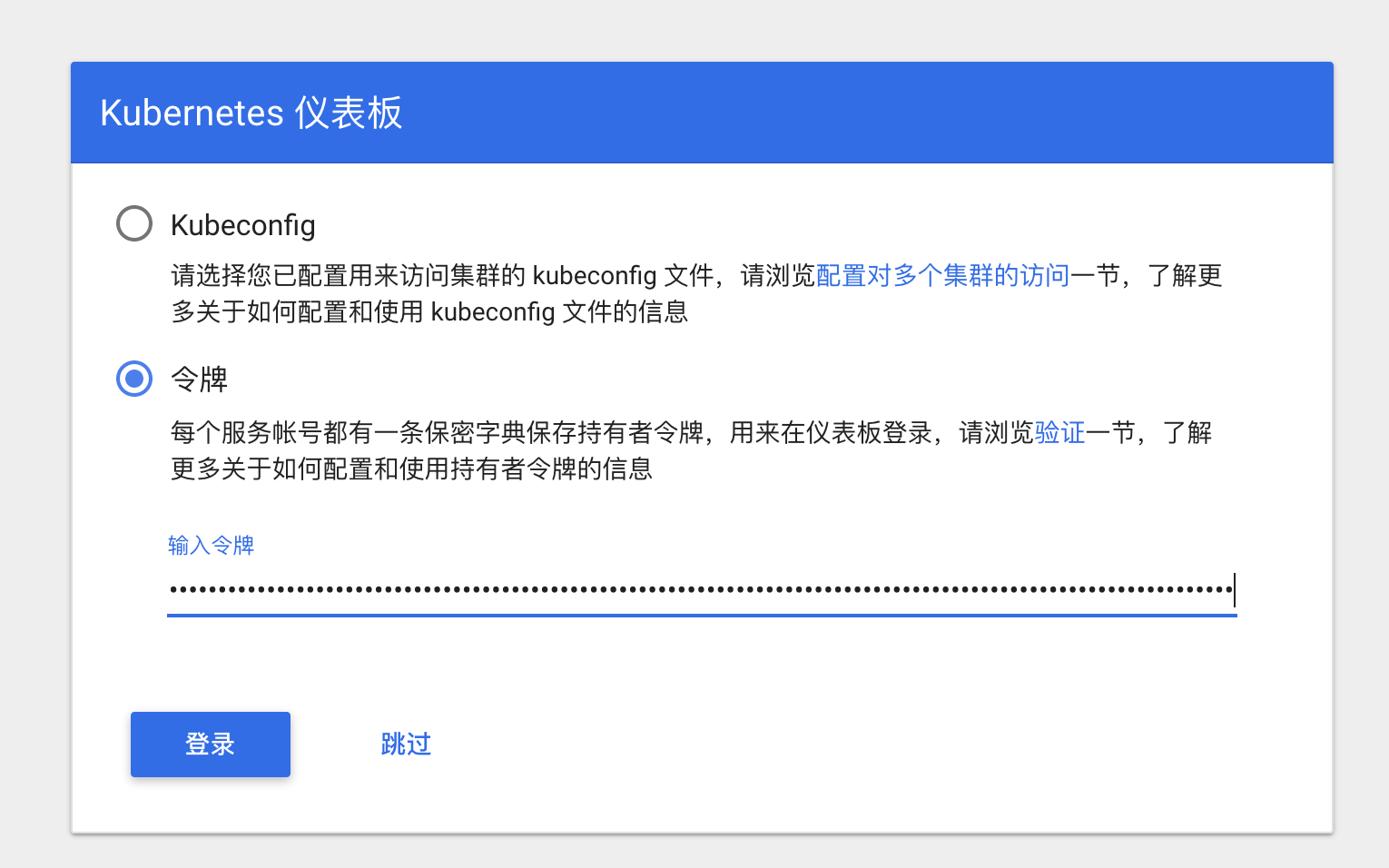
Kubeconfig文件认证
创建一个只对default命令空间有权限的账号
创建一个serviceaccount授权给admin # ------------------- Dashboard Service Account ------------------- # apiVersion: v1 kind: ServiceAccount metadata: name: def-ns-admin namespace: default --- # -------------------Dashboard Service Account rbac ------------------- # apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: creationTimestamp: null name: def-ns-admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: admin subjects: - kind: ServiceAccount name: def-ns-admin namespace: default
创建一个kubeconfig配置文件(基于token配置)
$ kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server=https://172.16.138.44:8443 --embed-certs=true --kubeconfig=/root/dashboard/def-ns-admin.conf 查看一下证书主体 $ kubectl config view --kubeconfig=./def-ns-admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: REDACTED server: https://172.16.138.44:8443 name: kubernetes contexts: [] current-context: "" kind: Config preferences: {} users: [] 通过user的token认证 对token进行转码 $ DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-4txrk -o jsonpath={.data.token} | base64 -d) $ kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/dashboard/def-ns-admin.conf 配置上下文 $ kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=./def-ns-admin.conf 查看配置文件 $ kubectl config view --kubeconfig=./def-ns-admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: REDACTED server: https://172.16.138.44:8443 name: kubernetes contexts: - context: cluster: kubernetes user: def-ns-admin name: def-ns-admin@kubernetes current-context: "" kind: Config preferences: {} users: - name: def-ns-admin user: token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi00dHhyayIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJhMzA5M2ZhOC1lMjVlLTExZTgtODI1Ni0wMDUwNTY5MzRiZTciLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.TsUqPXzgqzZE2QggL_N4-LDMxw0zxeCIHuhT0_Tua8K76BXlzl1XLk0Dwvqh_MjwkJVdXRKARWjm0mA2SWIp-3vRs6TaaeKK94uMd9BtnWe-j9LPMpbll5h-DJIP1DWm0MraXAO65x-QpjlzsjUSr555rpMLSZfioWSaG4w7eHLT4XR2EoLJqtwkAKTk_zFfv3h_26eSXgul204hxO9Nde6474QUKeugdFHAFrRgmyLM4HTSKoRvo12BvD5npIIzFCN76PYXaJxEwSgKtIffuj0XyvfdvAkRmcxoGaFfbeIGYdi0nZ06u1Q0ydfkZzK1s8aE7CaxU7OV3Hp8O0MqfA #配置当前上下文 $ kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/dashboard/def-ns-admin.conf #查看配置文件 $ kubectl config view --kubeconfig=/root/dashboard/def-ns-admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: REDACTED server: https://172.16.138.44:8443 name: kubernetes contexts: - context: cluster: kubernetes user: def-ns-admin name: def-ns-admin@kubernetes current-context: def-ns-admin@kubernetes kind: Config preferences: {} users: - name: def-ns-admin user: token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi00dHhyayIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJhMzA5M2ZhOC1lMjVlLTExZTgtODI1Ni0wMDUwNTY5MzRiZTciLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.TsUqPXzgqzZE2QggL_N4-LDMxw0zxeCIHuhT0_Tua8K76BXlzl1XLk0Dwvqh_MjwkJVdXRKARWjm0mA2SWIp-3vRs6TaaeKK94uMd9BtnWe-j9LPMpbll5h-DJIP1DWm0MraXAO65x-QpjlzsjUSr555rpMLSZfioWSaG4w7eHLT4XR2EoLJqtwkAKTk_zFfv3h_26eSXgul204hxO9Nde6474QUKeugdFHAFrRgmyLM4HTSKoRvo12BvD5npIIzFCN76PYXaJxEwSgKtIffuj0XyvfdvAkRmcxoGaFfbeIGYdi0nZ06u1Q0ydfkZzK1s8aE7CaxU7OV3Hp8O0MqfA
登录
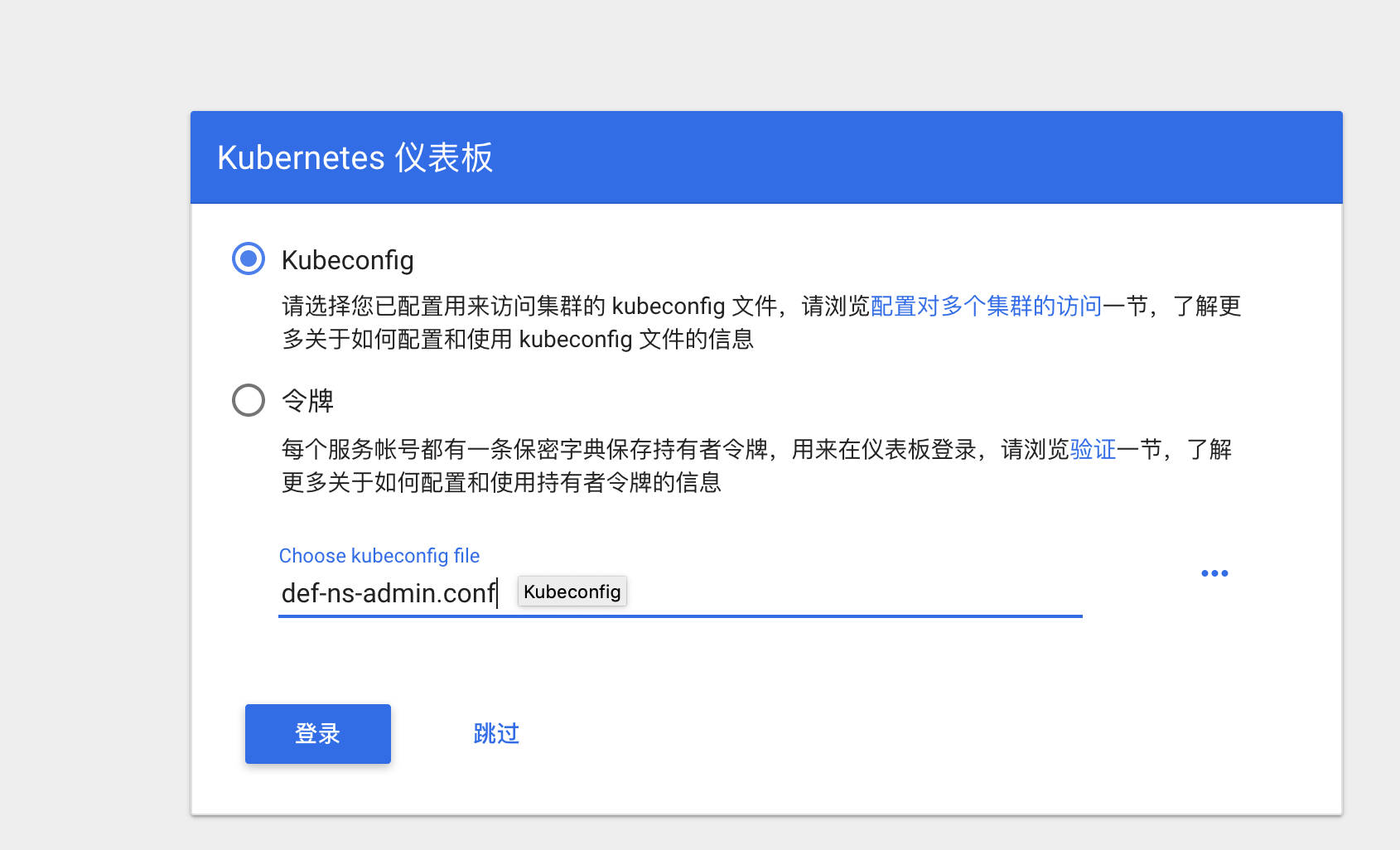
而且这里只能操作default命令空间
