转自:http://woshub.com/port-forwarding-in-windows/
Since Windows XP there is a built-in ability in Microsoft Windows to set up network ports forwarding. Due to it, any incoming TCP connection (IPv4 or IPv6) to local port can be redirected to another local port or even to port on the remote computer. And it is not necessary for system to have a service that listens to this port.
In Linux, port redirection is configured quite simply using iptables. On Windows Server systems, the Routing and Remote Access Service (RRAS) is used to organize port forwarding. However, there is an easier way to configure the port forwarding, which works well in any version of Windows.
Port forwarding in Windows can be configured using Portproxy mode of the command Netsh. The syntax of this command is as follows:netsh interface portproxy add v4tov4 listenaddress=localaddress listenport=localport connectaddress=destaddress connectport=destport
where
- listenaddress – is a local IP address waiting for a connection.
- listenport – local listening TCP port (the connection is waited on it).
- connectaddress – is a local or remote IP address (or DNS name) to which the incoming connection will be redirected.
- connectport – is a TCP port to which the connection from listenport is forwarded to.
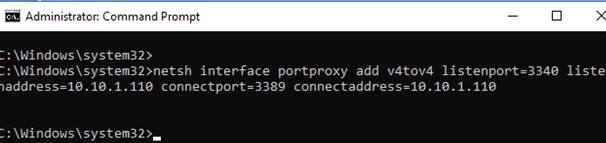
Let’s imagine that our task is to make the RDP service to respond on a non-standard port, for example 3340 (the port can be changed in the settings of the service, but we will use RDP to make it easier to demonstrate forwarding). To do this, you need to redirect incoming traffic from TCP port 3340 to another local port – 3389 (standard rdp port).
Start the command prompt as an administrator and perform the following command:
netsh interface portproxy add v4tov4 listenport=3340 listenaddress=10.1.1.110 connectport=3389 connectaddress=10.1.1.110
Where 10.10.1.110 – the current IP address of this computer.
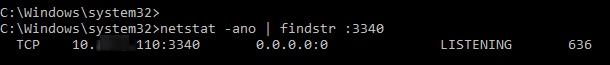
Using netstat make sure that port 3340 is listened now:
netstat -ano | findstr :3340
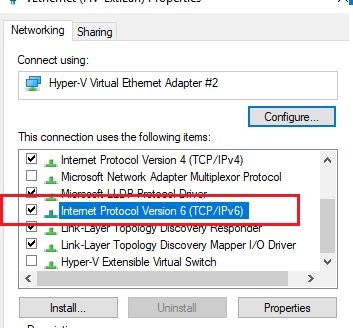
IPv6 support must be enabled on the network interface for which the port forwarding rule is created.
These are the prerequisites for correct port-forwarding. Without the IP Helper service and without IPv6 support enabled, the port redirection won’t work.
You can find out what process is listening to this port use its PID (in our example, the PID is 636):
tasklist | findstr 636
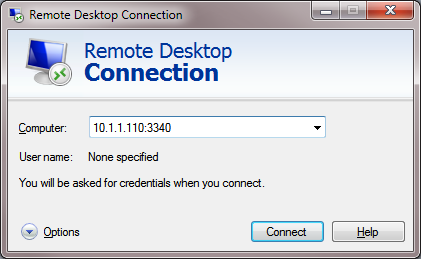
Let’s try to connect to this computer from a remote system using any RDP client. Port 3340 should be specified as the RDP port.It is specified after the colon following the RDP server address, for example, 10.10.1.110:3340:
The connection should be established successfully.
netsh advfirewall firewall add rule name=”forwarded_RDPport_3340” protocol=TCP dir=in localip=10.1.1.110 localport=3340 action=allow
When creating an incoming firewall rule for port 3340 via Windows Firewall graphical interface, no program needs to be associated with it. This port is only listened by the network driver.
You can create any number of Windows port forwarding rules. All netsh interface portproxy rules are persistent and are stored in the system after a Windows restart.
Display the list of forwarding rules in the system:
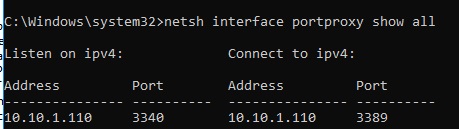
netsh interface portproxy show all
In our case there is only one forwarding rule from port 3340 to 3389:
Listen on ipv4: Connect to ipv4:
Address Port Address Port
--------------- ---------- --------------- ----------
10.1.1.110 3340 10.1.1.110 3389
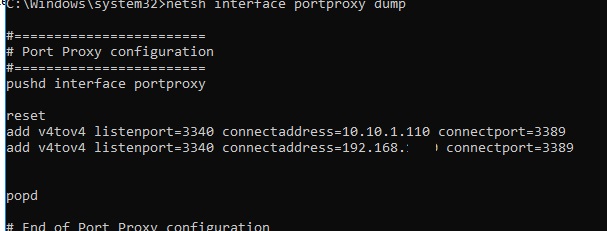
netsh interface portproxy dump#========================
# Port Proxy configuration
#========================
pushd interface portproxy
reset
add v4tov4 listenport=3340 connectaddress=10.1.1.110 connectport=3389
popd
# End of Port Proxy configuration
To remove a specific port forwarding rule:
netsh interface portproxy delete v4tov4 listenport=3340 listenaddress=10.1.1.110
To clear all current port forwarding rules:
netsh interface portproxy reset
If you want to forward an incoming TCP connection to another computer, the command can look like this:
netsh interface portproxy add v4tov4 listenport=3389 listenaddress=0.0.0.0 connectport=3389 connectaddress=192.168.100.101
This rule will redirect all incoming RDP requests (to port 3389) from this computer to a remote computer with an IP address 192.168.1.101.
Another portproxy feature is an opportunity to make it look like any remote network service is operating locally.
For example, forward the connection from the local port 5555 to the remote address 157.166.226.25 (CNN website):
netsh interface portproxy add v4tov4 listenport=5555 connectport=80 connectaddress= 157.166.226.25 protocol=tcp
Now if you go to http://localhost:5555/ in your browser, CNN Start page will open. So despite the browser addresses the local computer, it opens a remote page.
Port forwarding can also be used to forward a port from an external address of a network card to a virtual machine port running on the same computer.
Also, there were cases when in Windows Server 2012 R2 the port forwarding rules worked only until the system was rebooted, and after restart they were reset. In this case, you need to check whether there is a periodic disconnection on the network interface, and whether the IP address changes when the OS boots (it is better to use a static IP). As a workaround, I had to add a script to the Windows scheduler with the netsh interface portproxy rules that run on the system startup.
In Windows Server 2003 / XP, you must additionally set the IPEnableRouter parameter to 1 in the registry key HKLMSYSTEMControlSet001ServicesTcpipParameters.