问题详情
然后,执行,出现如下问题,则说明大家的这个文件,下载不是完整的或者你上传不完整。
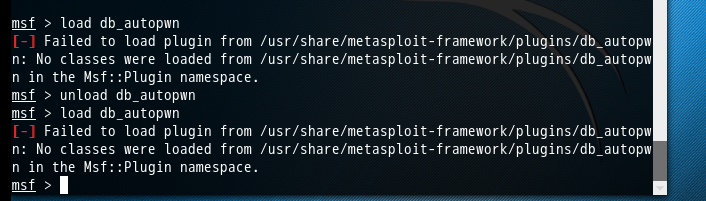
msf > load db_autopwn
[-] Failed to load plugin from /usr/share/metasploit-framework/plugins/db_autopwn: No classes were loaded from /usr/share/metasploit-framework/plugins/db_autopwn in the Msf::Plugin namespace.
解决办法
你也许会,像我也一样,第一次弄的时候,是先下载别人的,再上传。其实,这样,很有可能下载到的是别人的不完整或不干净的
我建议,大家按照如下来。
新版本取消了自动攻击模块 需要自己下载安装 下载地址:
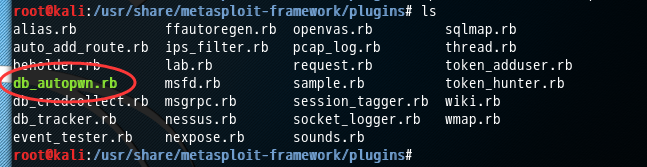
kali 安装路径 /usr/share/metasploit-framework/plugins 路径下面下载 db_autopwn.rb
地址:
https://github.com/neinwechter/metasploit-framework/blob/autopwn-modules/plugins/db_autopwn.rb

成功!
然后呢,大家要关闭终端,因为,你之前已经尝试过失败的,那个不靠谱的)db_autopwn的话,会报错。于是,可以按照我如下,重新来个完整的,就可以见到生效了。
root@kali:~# msfconsole Unable to handle kernel NULL pointer dereference at virtual address 0xd34db33f EFLAGS: 00010046 eax: 00000001 ebx: f77c8c00 ecx: 00000000 edx: f77f0001 esi: 803bf014 edi: 8023c755 ebp: 80237f84 esp: 80237f60 ds: 0018 es: 0018 ss: 0018 Process Swapper (Pid: 0, process nr: 0, stackpage=80377000) Stack: 90909090990909090990909090 90909090990909090990909090 90909090.90909090.90909090 90909090.90909090.90909090 90909090.90909090.09090900 90909090.90909090.09090900 .......................... cccccccccccccccccccccccccc cccccccccccccccccccccccccc ccccccccc................. cccccccccccccccccccccccccc cccccccccccccccccccccccccc .................ccccccccc cccccccccccccccccccccccccc cccccccccccccccccccccccccc .......................... ffffffffffffffffffffffffff ffffffff.................. ffffffffffffffffffffffffff ffffffff.................. ffffffff.................. ffffffff.................. Code: 00 00 00 00 M3 T4 SP L0 1T FR 4M 3W OR K! V3 R5 I0 N4 00 00 00 00 Aiee, Killing Interrupt handler Kernel panic: Attempted to kill the idle task! In swapper task - not syncing Frustrated with proxy pivoting? Upgrade to layer-2 VPN pivoting with Metasploit Pro -- learn more on http://rapid7.com/metasploit =[ metasploit v4.12.41-dev ] + -- --=[ 1597 exploits - 912 auxiliary - 274 post ] + -- --=[ 458 payloads - 39 encoders - 8 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf >
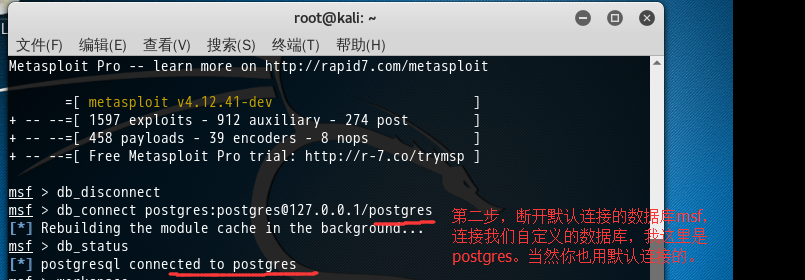
msf > db_disconnect msf > db_connect postgres:postgres@127.0.0.1/postgres [*] Rebuilding the module cache in the background... msf > db_status [*] postgresql connected to postgres msf >
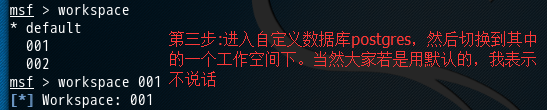
msf > workspace * default 001 002 msf > workspace 001 [*] Workspace: 001
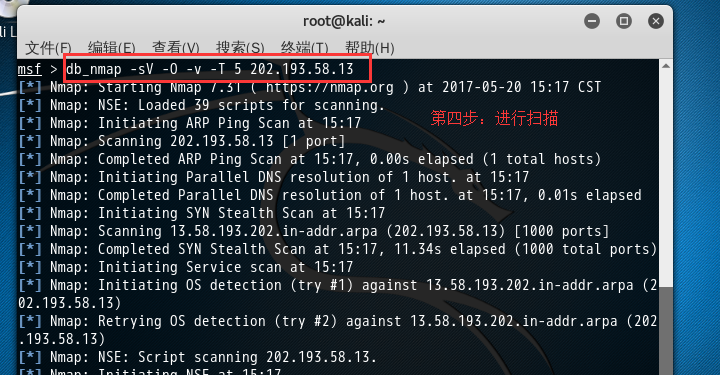
msf > db_nmap -sV -O -v -T 5 202.193.58.13 [*] Nmap: Starting Nmap 7.31 ( https://nmap.org ) at 2017-05-20 15:17 CST [*] Nmap: NSE: Loaded 39 scripts for scanning. [*] Nmap: Initiating ARP Ping Scan at 15:17 [*] Nmap: Scanning 202.193.58.13 [1 port] [*] Nmap: Completed ARP Ping Scan at 15:17, 0.00s elapsed (1 total hosts) [*] Nmap: Initiating Parallel DNS resolution of 1 host. at 15:17 [*] Nmap: Completed Parallel DNS resolution of 1 host. at 15:17, 0.01s elapsed [*] Nmap: Initiating SYN Stealth Scan at 15:17 [*] Nmap: Scanning 13.58.193.202.in-addr.arpa (202.193.58.13) [1000 ports] [*] Nmap: Completed SYN Stealth Scan at 15:17, 11.34s elapsed (1000 total ports) [*] Nmap: Initiating Service scan at 15:17 [*] Nmap: Initiating OS detection (try #1) against 13.58.193.202.in-addr.arpa (202.193.58.13) [*] Nmap: Retrying OS detection (try #2) against 13.58.193.202.in-addr.arpa (202.193.58.13) [*] Nmap: NSE: Script scanning 202.193.58.13. [*] Nmap: Initiating NSE at 15:17 [*] Nmap: Completed NSE at 15:17, 0.00s elapsed [*] Nmap: Initiating NSE at 15:17 [*] Nmap: Completed NSE at 15:17, 0.00s elapsed [*] Nmap: Nmap scan report for 13.58.193.202.in-addr.arpa (202.193.58.13) [*] Nmap: Host is up (0.0012s latency). [*] Nmap: All 1000 scanned ports on 13.58.193.202.in-addr.arpa (202.193.58.13) are filtered [*] Nmap: MAC Address: 84:AD:58:82:49:5C (Unknown) [*] Nmap: Too many fingerprints match this host to give specific OS details [*] Nmap: Network Distance: 1 hop [*] Nmap: Read data files from: /usr/bin/../share/nmap [*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . [*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 16.88 seconds [*] Nmap: Raw packets sent: 2049 (94.700KB) | Rcvd: 15 (1.528KB) msf > hosts Hosts ===== address mac name os_name os_flavor os_sp purpose info comments ------- --- ---- ------- --------- ----- ------- ---- -------- 202.193.58.13 84:AD:58:82:49:5C 13.58.193.202.in-addr.arpa embedded device
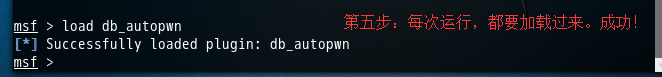
msf > load db_autopwn [*] Successfully loaded plugin: db_autopwn msf >
欧克,本博文解决问题,后续工作,我这不赘述。