About the software:
"Safe3 Web Protector" is a new generation of Web security technology based and on the full range of enterprise Web development of information security product produced by the well-known security organization Safe3 network . Not only can effectively scan a variety of WebShell, but also can withstand a variety of Web attacks.
Operating Environment:
The software can run on Windows 2000/2003 supporting IIS5/IIS6 .
Software main functions:
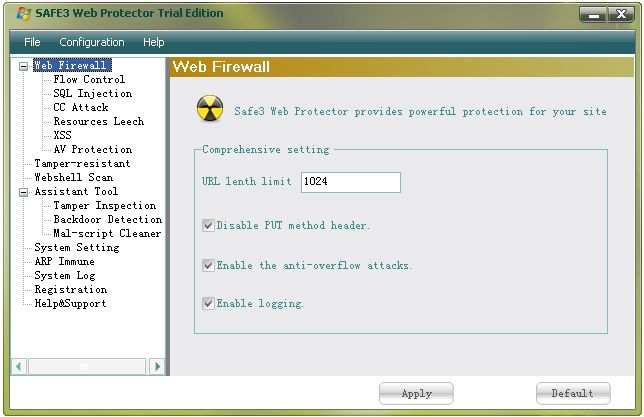
Flow control. Swamped with P2P network software, multi-threaded download (such as the Thunder, etc.) resulted in the only website bandwidth resources are severely depleted, not only affected the site normal browsing, but also for a large number of extra payment of the cost of the flow. Safe3 IIS Firewall can effectively solve the multi-threaded download traffic brought about by the loss, to help win the network station opportunities.
SQL injection. Today, a variety of SQL injection tools full of Internet, what is more automation of Mass SQL Injection Worm on the day can give tens of thousands of sites linked to trojan, serious damage to the corporate image and data security. Safe3 IIS Firewall into the simulation technology used to effectively block all kinds of variants of implantation, to help enterprises in the Internet Network to turn the tide and win living space.
CC attack. An increasingly competitive on the Internet today, unfair competition caused by the other side of the grave site of the CC attack, followed by net freight terminal and a sharp decline in traffic. Strong Safe3 IIS Firewall to stop DDOS attacks CC caused a thorough solution to illegal improper competition.
Resources leech. Copy of today's inter-site resources (picture and download link) has been used, not only a waste of bandwidth resources, but also a tort. Safe3 IIS Firewall Web resources can be a high degree of protection while navigating to prevent, protect the original site of the legitimate rights and interests.
XSS Cross Site. OWASP will XSS as a security threat in 2007 the first WEB. Hackers to insert malicious Web page in html code, when a user views at the time of the page embedded inside the Web which will be the implementation of html code in order to achieve the specific purpose of a malicious user. Safe3 IIS Firewall testing can effectively contain the evil XSS URL and intended to intercept.
AV protection. Only allowed to play audio and video online and can not be directly downloaded from the protection of powerful video site bandwidth resources and quality of service.
Tamper-resistant. Web directory of real-time monitoring of changes and alarm, power to stop the page has been tampered with.
Webshell scan. Analysis can be scanned through the 99% of the hidden WebShell, the protection of web security.
Tampering inspection. Extract the characteristics of important documents, when the web page code can be changed rapidly from a large number of code files to find hidden in the back door or Trojan horse page.
Backdoor detection. Mainly used to detect the existence of a file Win2003 path vulnerability analysis, when hack.asp folder named similar to the time (that is, the folder who looks like an ASP file name), at this point in the text folder type of file can be in the IIS as ASP procedures to implement. Similar to the xxx .. \ such a special folder will be hackers to use. This folder can not have both the common deletion can not be changed, on the inside of some anti-virus software as Trojan horse and this feature can effectively find such a folder.
Mal-script cleaner. Online procedure volume of horses hanging everywhere, and to the administrator caused by hand to remove a lot of difficulties, this feature makes it easy to solve the plight of the administrator.
Arp immune. ARP linked to trojan and to prevent sensitive information being intercepted by eavesdropping. When hacking the same network segment of the host after the host if you did not make any defensive measures ARP, while your hosts are not black but customers visit your site by inserting malicious code page that is linked to Ma ARP. At the same time, hackers can sniff this network segment so the next host ftp, http, such as user passwords. Well-known hacker site security has been the focus of such attacks. Although the basic solution to the arp on the local threat. But also Gateway by deception, this will result in disruption of local communications, so I hope the best friend of conditional binding at the gateway on the local ip and mac address.
Software features:
Firewall using C language, a high operating efficiency 100 megabits per second data transmission good running on large servers, taking up very little CPU.
Do not write the registry, not tied to any plug-in, pure green pollution-free software.
Super security: anti-radical attacks SQL injection attacks.
Thoroughly anti-Thunderbolt, FlashGet and so on.
Without restarting IIS, configuration data, effective immediately.
Safe3 network security together for many years of experience, a strong and reliable.
Easy to install, configure, simple and rich guide to help document the installation, a dedicated configuration tool for easy configuration.
Download:http://121.207.254.246/safe3.zip
Technical Support: s0_6@hotmail.com
Contact: http://www.safe3.com.cn/