30.3 Architectural Model
Despite the potential disadvantages, having TCP/IP management software operate at the application level has worked well in practice. The most significant advantage of placing network management protocols at a high level becomes apparent when one considers a large internet, where a manager's computer does not need to attach directly to all physical networks that contain managed entities. Figure 30.1 shows an example of the architecture.
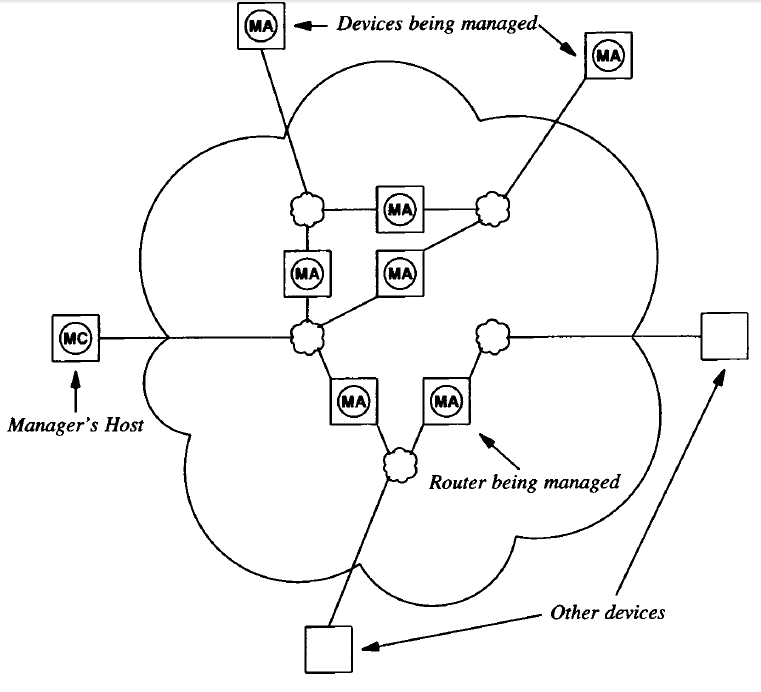

As the figure shows, client software usually runs on the manager's workstation. Each participating router or host1 runs a server program. Technically, the server software is called a management agent or merely an agent. A manager invokes client software on the local host computer and specifies anagent with which it communicates. After the client contacts the agent, it sends queries to obtain information or it sends commands to change conditions in the router. Of course, not all devices in a large internet fall under a single manager. Most managers only control devices at their local sites; a large site may have multiple managers.
Internet management software uses an authentication mechanism to ensure only authorized managers can access or control a particular device. Some management protocols support multiple levels of authorization, allowing a manager specific privileges on each device. For example, a specific router could be configured to allow several managers to obtain information while only allowing a select subset of them to change information or control the router.
1 Recall that the TCP/IP term hostcan refer to a device (e.g., a printer) or a conventional computer.
Abstract from Internetworking With TCP/IP Vol I: Principles, Protocols, and Architecture Fourth Edition,
DOUGLAS E. COMER,
Department of Computer Sciences Purdue University, West Lafayette, IN 47907,
PRENTICE HALL,
Upper Saddle River, New Jersey 07458