环境为CentOS 7.3、httpd2.4.6
一 搭建证书
说明:
CA 主机为192.168.29.3
client主机为 192.168.29.100
1 生成私钥
[root@centos7 ~]# (umask 077 ; openssl genrsa -out /etc/pki/CA/private/cakey.pem 4096)
Generating RSA private key, 4096 bit long modulus
.....................++
...........................................................................................................................................................................................++
e is 65537 (0x10001)
2 生成自签证书
[root@centos7 ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BeiJing
Locality Name (eg, city) [Default City]:BeiJing
Organization Name (eg, company) [Default Company Ltd]:Company
Organizational Unit Name (eg, section) []:OPS
Common Name (eg, your name or your server's hostname) []:www.test.com
Email Address []:
[root@centos7 ~]#
3 为CA提供所需的目录及文件
(1)所需目录,如果无,则创建
/etc/pki/CA/certs/
/etc/pki/CA/crl/
/etc/pki/CA/newcerts/
(2)所需文件
[root@centos7 ~]# touch /etc/pki/CA/serial #序列号文件
[root@centos7 ~]# touch /etc/pki/CA/index.txt #数据库文件
(3)
[root@centos7 ~]# echo 01 > /etc/pki/CA/serial #维护ca的序列号
4 在client上进行如下操作
(1)创建放置公钥私钥的文件夹
[root@CentOS7 ~]# mkdir /etc/httpd/ssl
(2)生成自己的私钥
[root@CentOS7 ~]# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
Generating RSA private key, 2048 bit long modulus
.......................................+++
...................................+++
e is 65537 (0x10001)
[root@CentOS7 ~]#
(3)请CA为自己生成公钥
[root@CentOS7 ~]# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BeiJing
Locality Name (eg, city) [Default City]:BeiJing
Organization Name (eg, company) [Default Company Ltd]:Company
Organizational Unit Name (eg, section) []:OPS
Common Name (eg, your name or your server's hostname) []:www.test.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
(4)把生成的公钥发送给CA
[root@CentOS7 ~]# scp /etc/httpd/ssl/httpd.csr root@192.168.29.3:/tmp/
The authenticity of host '192.168.29.3 (192.168.29.3)' can't be established.
ECDSA key fingerprint is f2:2e:89:a2:8d:22:22:9c:a9:f8:c9:19:18:d3:b6:c4.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.29.3' (ECDSA) to the list of known hosts.
root@192.168.29.3's password:
httpd.csr 100% 1005 1.0KB/s 00:00
5 在CA主机上为client签证
[root@centos7 ~]# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jun 3 02:54:23 2017 GMT
Not After : Jun 3 02:54:23 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
organizationName = Company
organizationalUnitName = OPS
commonName = www.test.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5D:A9:5A:90:29:F3:3A:7F:76:BE:21:78:14:80:E5:FB:5E:03:D8:D9
X509v3 Authority Key Identifier:
keyid:9E:1E:F3:84:4D:D0:79:E2:BD:DD:A8:50:29:6C:BA:0C:21:60:CA:96
Certificate is to be certified until Jun 3 02:54:23 2018 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
6 把签署的证书发给client
[root@centos7 ~]# scp /etc/pki/CA/certs/httpd.crt root@192.168.29.100:/etc/httpd/ssl/
The authenticity of host '192.168.29.100 (192.168.29.100)' can't be established.
ECDSA key fingerprint is 32:16:f3:2d:78:65:9f:a0:31:6c:dc:b9:24:e7:5a:8f.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.29.100' (ECDSA) to the list of known hosts.
root@192.168.29.100's password:
httpd.crt 100% 5711 5.6KB/s 00:00
二 HTTPS配置
7 安装mod_ssl模块
[root@CentOS7 ~]# yum install mod_ssl -y
8 修改配置文件/etc/httpd/conf.d/ssl.conf
DocumentRoot "/data/https"
ServerName www.test.com:443
<Directory "data/https">
AllowOverride None
Require all granted
</Directory>
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
注意:
并修该/etc/httpd/ssl/httpd.crt、/etc/httpd/ssl/httpd.key两个文件的属性,确保apach为可读就行,当然也可放在默认文件夹下,就不需要修改权限了。
[root@CentOS7 ~]#chmod +r /etc/httpd/ssl/httpd.key
9 检查语法
[root@CentOS7 ~]# httpd -t
Syntax OK
10 修给默认页面
[root@CentOS7 ~]# echo "www.test.com" > /data/https/index.html
11 启动http服务
[root@CentOS7 ~]# systemctl start httpd.service
12 把CA 的自签证书传到桌面
[root@centos7 ~]# sz /etc/pki/CA/cacert.pem
改名为cacert.crt
双击导入IE浏览器
13 配置DNS解析
www.test.com 为192.168.29.100
或者 修改windows 下的C:WindowsSysteme32driversetchosts文件
192.168.29.100 www.test.com
14 打开IE浏览器测试
输入https://www.test.com
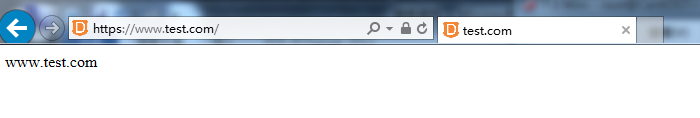
好了 成功了 好用成就感呀!!