Wifite v2 is now available
What's new in this version:
- support for cracking WPS-encrypted networks (via reaver)
- 2 new WEP attacks
- more accurate WPA handshake capture
- various bug fixes
Version 2 does not include a GUI, so everything must be done at the command-line.
mention in the New York Times
Wifite was mentioned in the New York Times' article "New Hacking Tools Pose Bigger Threats to Wi-Fi Users" from February 16, 2011. Here is a link to the article.
introduction
Designed and tested on Linux; works with Backtrack 5, BlackBuntu, BackBox, and Pentoo! Linux only; no windows or OSX support (but you're welcome to try).
purpose
To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the "set it and forget it" wireless auditing tool.
features
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- "anonymous" feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py's current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- built-in updater: ./wifite.py -upgrade
requirements
- linux operating system (confirmed working on Backtrack 5, BackBox, BlackBuntu, Pentoo, Ubuntu 8.10 (BT4R1), Ubuntu 10.04, Debian 6, Fedora 16)
- tested working with python 2.6.x, and python 2.7.x,
- wireless drivers patched for monitor mode and injection. Most security distributions (Backtrack, BlackBuntu, etc) come with wireless drivers pre-patched,
- aircrack-ng (v1.1) suite: available via apt: apt-get install aircrack-ng or at the aircrack-ng website,
suggested applications
- reaver, for attacking WPS-encrypted networks
- pyrit, cowpatty, tshark: not required, but help verify WPA handshake captures
For help installing any of these programs, see the installation guide (hosted on github)
execution
download the latest version:
wget -O wifite.py http://wifite.googlecode.com/svn/trunk/wifite.py
change permissions to executable:
chmod +x wifite.py
execute:
python wifite.py
or, to see a list of commands with info:
./wifite.py -help
screenshots
successful WEP attack (after 90 seconds):
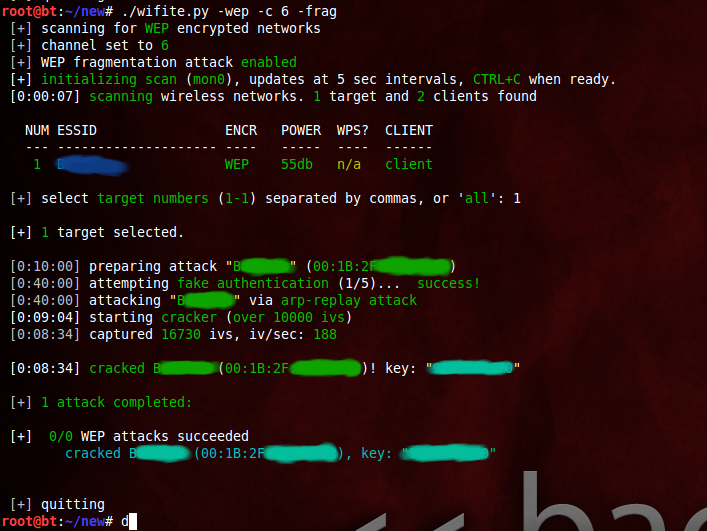
successful WPS attacks (after 17 hours):

examples
the program contains lots of interactivity (waits for user input). these command-line options are meant to make the program 100% automated -- no supervision required.
to crack all WEP access points:
./wifite.py -all -wep
to crack all WPS access points with signal strength greater than (or equal to) 50dB:
./wifite.py -p 50-wps
to attack all access points, use 'darkc0de.lst' for cracking WPA handshakes:
./wifite.py -all --dict /pentest/passwords/wordlists/darkc0de.lst
to attack all WPA access points, but do not try to crack -- any captured handshakes are saved automatically:
./wifite.py -all -wpa --dict none
to crack all WEP access points greater than 50dB in strength, giving 5 minutes for each WEP attack method, and send packets at 600 packets/sec:
./wifite.py --pow 50-wept 300-pps 600
to attempt to crack WEP-encrypted access point "2WIRE752" endlessly -- program will not stop until key is cracked or user interrrupts with ctrl+C):
./wifite.py -e "2WIRE752"-wept 0